Export Pcap to CSV
Introduction
Exporting data from PCAP (Packet Capture) files to CSV format is a fundamental skill for network administrators and cybersecurity professionals. PCAP files contain detailed information about network traffic and are often used for network diagnostics and forensic analysis.
This guide provides step-by-step instructions for converting PCAP files to CSV format. You'll gain insights into the essential tools and commands needed to perform the conversion efficiently.
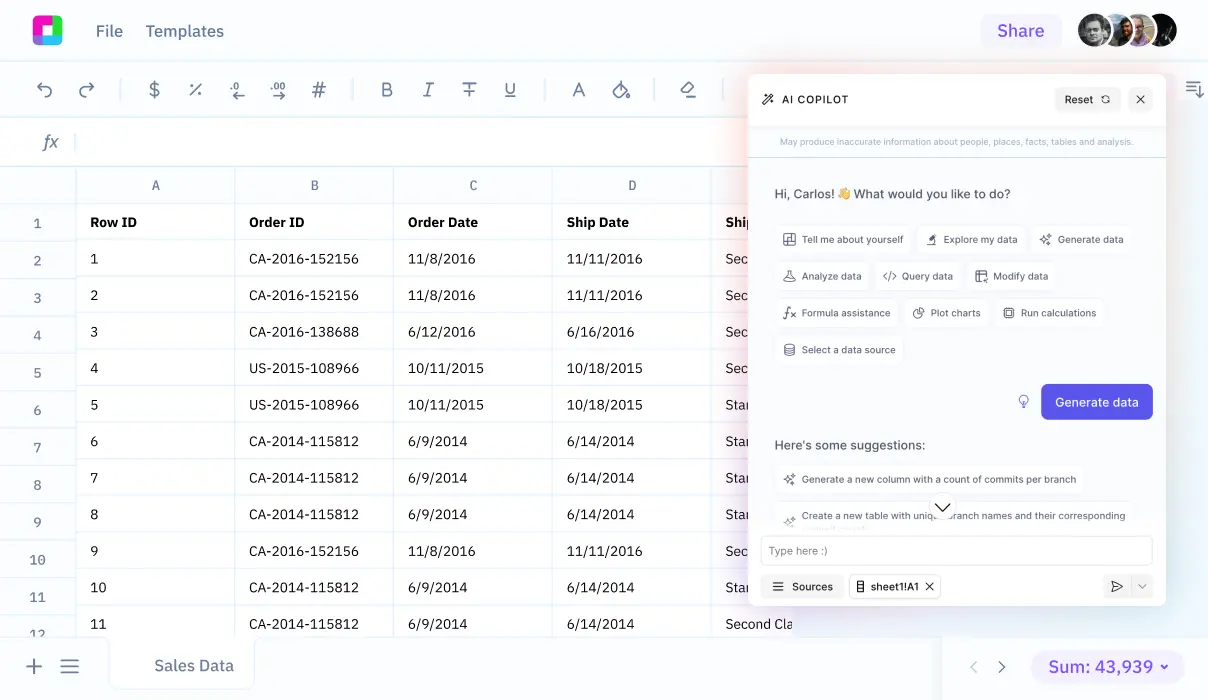
Additionally, we will explore how Sourcetable lets you analyze your exported data with AI in a simple to use spreadsheet.
Exporting Data to CSV Format from PCAP Files
Using Wireshark
Wireshark is a popular tool that can output dissected packets as a .csv file. To start, open the .pcap file with Wireshark. Once the file is open, use filters to select the specific packets you want to export. Filtering ensures that only the relevant data is included in the output file.
After filtering, navigate to File -> Packet Dissections -> As CSV ... to export the data. If you want to export only the filtered packets, ensure that you select Displayed in the Packet Range option. Finally, save your file to complete the export process.
Using tshark
tshark is another powerful tool that can convert .pcap files to .csv format. This command-line tool offers a flexible option for users who prefer working with text-based interfaces. To use tshark for export, you can utilize the -T option to specify the desired format.
For more refined control, tshark allows you to filter packets and define specific fields to include in the CSV. This can be done with options like -T fields and -e field_name. This method is particularly useful for automation and scripting purposes.
Using Zeek
Zeek is a high-performance network analysis framework. While Zeek does not directly export .pcap to CSV, it can parse many protocols and output them as log files in tab-separated or JSON formats. These logs can then be converted into CSV as needed.
This method is practical for in-depth analysis and large-scale data processing. By leveraging Zeek's parsing capabilities, users can obtain detailed logs that are easily convertible to CSV format for further analysis.
How to Export PCAP Data to CSV Format
Using Wireshark
Wireshark can output dissected packets as CSV files. To export packets, open your .pcap file in Wireshark. Apply filters to select the packets you want to export. Go to File > Packet Dissections > As CSV. Use the Displayed in Packet Range option to export only the filtered packets. Save the file to complete the process.
Using Tshark
Tshark, the command-line version of Wireshark, is another tool that can convert PCAP data to CSV format. Use the -T option to specify CSV output. This method is efficient for batch processing or automation tasks.
Using Zeek
Zeek is a powerful network analysis tool that can parse protocols and output the data in CSV format. This option is useful if you need detailed protocol parsing and logging capabilities in addition to a simple CSV export.
By following these steps using Wireshark, Tshark, or Zeek, you can efficiently export your PCAP data to CSV format for further analysis or reporting.
Use Cases Unlocked by PCAP
Network Utilization Analysis
Packet capture (PCAP) is essential for analyzing network utilization. By intercepting and recording data packets, network administrators can monitor bandwidth usage and traffic patterns, identifying who is consuming the most bandwidth and what protocols are in use. This helps in optimizing network performance and managing resources effectively.
Diagnosing Slow Response Times
PCAP is useful in diagnosing slow response times in network communications. By examining the captured packets, IT teams can determine if the delays are due to network issues or application-level problems, allowing for precise troubleshooting and faster resolution of performance issues.
Identifying Security Flaws and Breaches
PCAP is a powerful tool for cybersecurity. It enables IT teams to identify security flaws, detect breaches, and monitor for intrusion attempts. By analyzing packet data, teams can spot unusual activity, sudden spikes in traffic, and data leaks, facilitating prompt and effective incident response.
Reconstructing and Understanding Attacks
PCAP is invaluable for reconstructing cyberattacks. By analyzing the captured packets, security teams can understand the attack sequence, validate intrusions, and develop robust remediation plans. This deep visibility into network traffic is crucial for defending against future threats and addressing zero-day exploits.
Monitoring Network Behavior
PCAP is essential for continuous monitoring of network behavior. It helps detect malicious activity, validate network intrusions, and simulate network conditions for testing. This real-time analysis of network traffic ensures compliance and enhances overall network security.
Managing Network Traffic and Congestion
PCAP is used to manage network traffic and detect congestion issues. By capturing and analyzing data packets, IT teams can identify packet loss, network congestion, and areas of high traffic volume. This information is critical for maintaining network performance and ensuring efficient data flow.
Tracking Network Usage and Detecting Misuse
With PCAP, IT teams can track overall network usage and detect misuse. By examining packet captures, they can monitor who is accessing the network, isolate compromised systems, and identify rogue devices such as unauthorized DHCP servers, ensuring a secure and well-managed network environment.
Validating Intrusions and Developing Defenses
PCAP plays a vital role in validating intrusions and preparing defenses for new attacks. By analyzing packet data, IT teams can identify and understand zero-day exploits, which do not trigger standard alerts or have known signatures. This proactive defense mechanism helps in fortifying network security.
Why Choose Sourcetable Over PCAP
Sourcetable offers a unified solution for data management by aggregating data from various sources into one cohesive spreadsheet interface. This capability eliminates the need for multiple tools, providing a streamlined workflow for your data operations.
With Sourcetable, users benefit from real-time database querying, enabling instant access to up-to-date information. This feature ensures that decision-making is based on the latest data, which is crucial for maintaining accuracy and relevance in dynamic environments.
Sourcetable's spreadsheet-like interface makes data manipulation intuitive, reducing the learning curve associated with traditional databases. This ease of use allows teams to quickly adapt and perform data analysis without extensive training.
Compared to PCAP, Sourcetable enhances efficiency by consolidating tools and offering direct access to live data, ultimately empowering users to make informed decisions faster. Its user-friendly interface further simplifies complex data tasks, making it an ideal choice for versatile data management.
Frequently Asked Questions
Can Wireshark export PCAP files to CSV format?
Yes, Wireshark can output dissected packets as .csv files.
How do I convert a PCAP file to a CSV file using Wireshark?
To convert a PCAP file to a CSV file using Wireshark, open the .pcap file with Wireshark, filter the packets you want to export, go to File->Packet Dissections->As CSV, and save the file.
Can I filter packets in Wireshark before exporting to CSV?
Yes, you can filter the packets you want to export in Wireshark before converting to CSV.
How can I convert a PCAP file to CSV using tshark?
You can use tshark with the -T option in the command line to convert a PCAP file to CSV format.
What is an alternative tool to Wireshark and tshark for exporting PCAP data to CSV?
Zeek is an alternative tool that can parse many protocols and output them as logs in CSV format.
Conclusion
Exporting data from PCAP to CSV enables you to leverage your captured network traffic data effectively. Performing this conversion ensures compatibility with various data analysis tools.
Once exported, your CSV files can be easily manipulated and examined for deeper insights. Sign up for Sourcetable to analyze your exported CSV data with AI in a simple-to-use spreadsheet.