Export Nsg Rules to CSV
Introduction
Exporting data from NSG rules to CSV format is an essential task for network security management. This process allows you to review and analyze your NSG configurations effectively. CSV is a versatile format that is widely used for data manipulation and reporting.
In this guide, we will provide step-by-step instructions on how to export NSG rules to CSV format. We will also discuss common issues and troubleshooting tips to ensure a smooth export process.
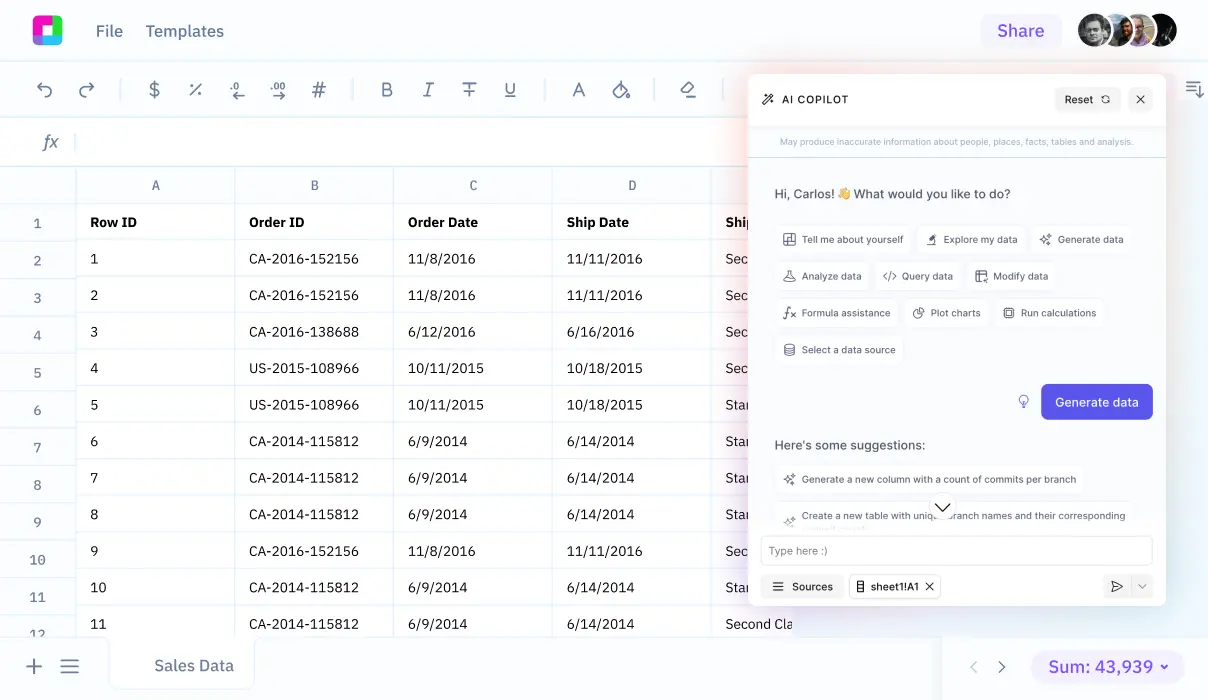
Additionally, we will explore how Sourcetable lets you analyze your exported data with AI in a simple-to-use spreadsheet.
Exporting NSG Rules to CSV Format
Required Permissions
To export NSG rules, you must have co-administrator access at the subscription level. This permission level is necessary to access and export rules from classic resources.
PowerShell Commands
The main command to export NSG rules is Get-AzureNetworkSecurityGroup. Use the -Name parameter to specify the specific NSG you want to export, and the -Detailed switch to include detailed information about the NSG.
Exporting to CSV
To save the NSG rules to a CSV file, pipe the output to the Export-Csv cmdlet. The full command is: Get-AzureNetworkSecurityGroup -Name "Group" -Detailed).Rules | Export-Csv -Path C:\NSG01.csv -NoTypeInformation. This command exports the detailed rules to a specified path in CSV format without type information.
Limitations
Exporting NSG rules to CSV is not supported for Access Control Lists (ACLs) from Classic deployments. Ensure you are dealing with the correct deployment type before attempting the export.
Alternative Commands
For environments managed with the newer Az module, use Get-AzNetworkSecurityGroup to get all NSGs and Get-AzNetworkSecurityRuleConfig to get the rules for each NSG. This can be beneficial if you need a broader data set or are using updated modules.
How to Export NSG Rules to CSV Format
Prerequisites
To export Network Security Group (NSG) rules to a CSV file, you must be a co-administrator of the classic resources at the subscription level. This allows access to export the rules.
Using PowerShell to Export NSG Rules
The PowerShell command to export NSG rules to a CSV file involves several steps. First, use the `Get-AzureNetworkSecurityGroup` cmdlet with the `-Name` parameter to specify the NSG you want to export. Include the `-Detailed` switch to fetch detailed information about the NSG.
Command Syntax
Here's the command syntax to export NSG rules to a CSV file:
(Get-AzureNetworkSecurityGroup -Name "Group" -Detailed).Rules | Export-Csv -Path C:\NSG01.csv -NoTypeInformation
This command retrieves detailed rules for the specified NSG and pipes the output to the `Export-Csv` cmdlet to save it in the specified file path.
Limitations
Note that this command is applicable only for classic NSGs. It does not work with ARM (Azure Resource Manager) NSGs.
Alternative Method
You can also use the Effective Security Rules in NSG to download the rules directly if you prefer an alternative method to exporting via PowerShell.
Use Cases for Network Security Group (NSG) Rules
Filtering Traffic Between Azure Resources
Network security groups can filter network traffic between Azure resources within a virtual network. By specifying security rules for each Azure resource, you can effectively manage and control traffic flow, enhancing the security posture of your cloud infrastructure.
Controlling Inbound and Outbound Traffic
NSG rules allow you to precisely control the inbound and outbound network traffic to and from several types of Azure resources. By defining rules for sources, destinations, ports, and protocols, you can enforce strict access controls and ensure that only authorized traffic is permitted.
Augmenting Security with IP Addresses
Network security groups can augment security rules by allowing the specification of multiple individual IP addresses and ranges. This flexibility enables you to create sophisticated security policies that can address complex networking scenarios in a scalable manner.
Simplifying Security Definitions
Network security groups simplify the process of defining security for virtual networks. By using service tags, application security groups, and specifying ranges, you can reduce the number of individual rules needed, making management more straightforward and less prone to errors.
Applying NSG Rules During IP Translation
NSG rules are processed after Azure translates a public IP address to a private IP address for inbound traffic and before the translation in the opposite direction for outbound traffic. This ensures that your security policies are enforced consistently across both public and private interfaces.
Examples of Security Rules
Common NSG rule examples include AllowVNetInBound, AllowAzureLoadBalancerInBound, DenyAllInbound, AllowVnetOutBound, AllowInternetOutBound, and DenyAllOutBound. These predefined rules can serve as templates for creating custom policies tailored to your specific requirements.
Managing Rules for Network Interfaces
A network security group is associated with the network interface of an Azure resource, such as a virtual machine. This association allows you to apply specific security rules that govern the network behavior of individual resources, ensuring tight security control at the granular level.
Specifying Rule Details
Each NSG rule specifies details such as the source and destination IP ranges, ports, protocols, traffic direction, and the action to allow or deny traffic. This granularity enables precise control over network activity, facilitating the enforcement of robust security policies.
Why Choose Sourcetable Over NSG Rules
Sourcetable is a powerful alternative to NSG Rules, offering a unified platform for data aggregation. It collects data from numerous sources, streamlining your processes.
With Sourcetable's real-time database querying, users can effortlessly access and manipulate data. The intuitive spreadsheet-like interface simplifies data analysis and reporting.
Sourcetable's robust features offer efficiency and precision in data handling, making it an ideal choice for businesses looking to enhance their data management capabilities.
Frequently Asked Questions
What command is used to export NSG rules to a CSV file using PowerShell?
The command is Get-AzureNetworkSecurityGroup -Name "Group " -Detailed).Rules | Export-Csv -Path C:
Do I need any specific permissions to run the PowerShell command for exporting NSG rules?
Yes, you must be a co-administrator to run the command.
Can NSG rules from a classic NSG be directly imported into an ARM NSG?
No, ACLs exported from Classic deployment cannot be directly imported to ARM NSGs. You must manually enter the data into a new NSG in ARM.
What does the -Detailed argument in the PowerShell command specify?
The -Detailed argument specifies the name of the 'Group' and is used to get detailed information about the NSG rules.
How can I handle the exported NSG rules if I need to import them into an ARM NSG?
After exporting the NSG rules to CSV, you can use Excel to manually enter the data into a new NSG in ARM.
Conclusion
Exporting your NSG rules data to CSV is a straightforward process that ensures your data is accessible and easy to manipulate. This method allows for seamless integration with various tools and platforms.
By exporting your data to a CSV file, you enhance your ability to perform in-depth analysis and generate insightful reports.
Sign up for Sourcetable to analyze your exported CSV data with AI in a simple to use spreadsheet.