Export Nmap to CSV
Introduction
Nmap is a powerful network scanning tool used for network discovery and security auditing. Exporting data from Nmap to a CSV format is essential for in-depth analysis and reporting. In this guide, we will walk you through the steps to export Nmap scan results to CSV.
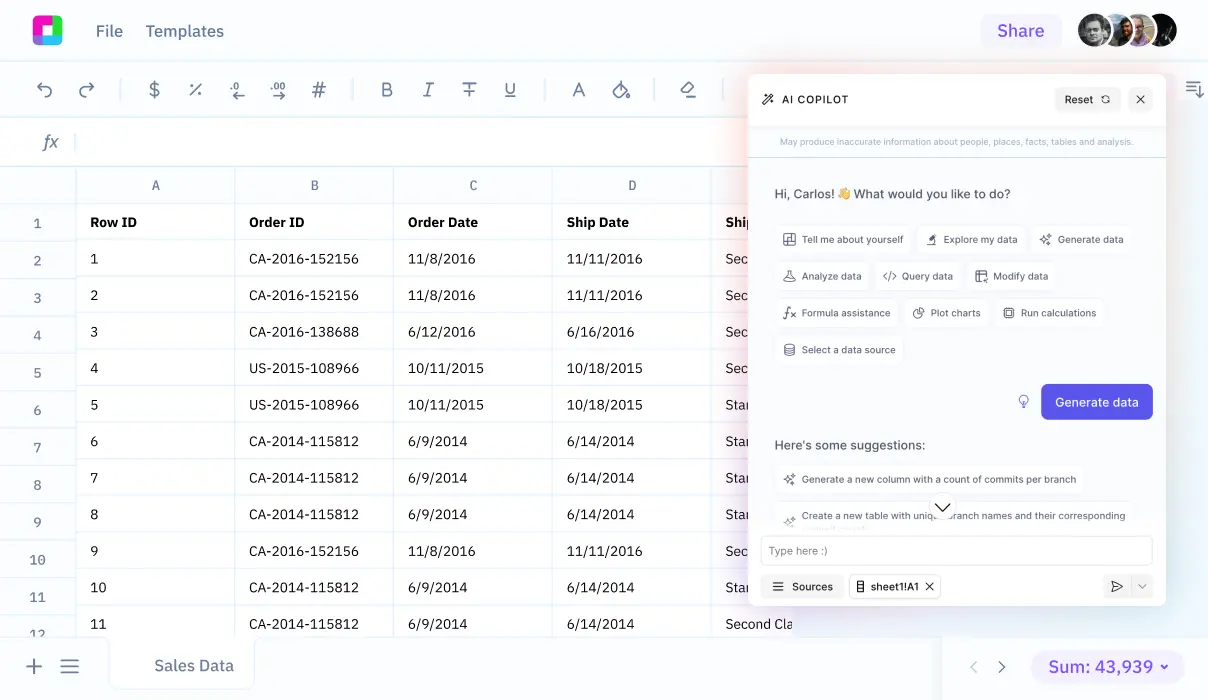
Once you've exported your data, you'll explore how Sourcetable lets you analyze your exported data with AI in a simple to use spreadsheet.
Exporting Nmap Data to CSV Format
Overview of Nmap Output Options
Nmap, a powerful network scanning tool, offers several output formats for storing scan results. These formats include XML, HTML, and grepable. By default, Nmap can save results in a "normal" output format. For more comprehensive data storage, use the XML format, which can be easily parsed by programs and converted to other formats. Nmap also supports saving results in all these formats simultaneously using the -oA option.
Using Nmap XML for Conversion
To export Nmap data to CSV, start by saving the scan results in XML format. This format is versatile and allows for easy conversion to other formats. Nmap provides several commands for customizing XML output, such as appending to existing files or resuming scans. You can also enhance the XML output with different XSL stylesheets or omit the XSL stylesheet altogether.
Converting Nmap XML to CSV
Once you have the Nmap scan results in XML format, use a conversion tool to transform the data into CSV format. The python script available in the NetsecExplained GitHub repository is one such tool that efficiently converts Nmap XML output to CSV. This script ignores hosts that are down and ports that are not open, providing clean and relevant data.
Advantages of sevenlayers Nmap - xml2csv
Another conversion tool, sevenlayers Nmap - xml2csv, also converts Nmap XML output to CSV and offers additional useful functions. Like the script from NetsecExplained, it ignores inactive hosts and closed ports, ensuring a focused dataset. This tool offers a more organized way to handle Nmap data compared to using the -oN flag.
Best Practices
When exporting Nmap data to CSV, it is important to start with XML output due to its versatility and ease of conversion. Use proven tools like the sevenlayers Nmap - xml2csv or the python script from NetsecExplained for reliable conversion. Always ensure that irrelevant data, such as down hosts and unopened ports, are filtered out to maintain a clean and actionable dataset.
How to Export Nmap Data to CSV
Overview
Exporting Nmap scan results to CSV format is crucial for data analysis and organization. Nmap supports multiple output formats, which can be converted to CSV for ease of use. This tutorial covers the most effective methods to save and convert your Nmap results to CSV.
Nmap Output Formats
Nmap offers several output formats including interactive mode, XML, grepable, normal, and sCRiPt KiDDi3. Though grepable output is deprecated, XML remains a robust and extensible format that is easily parsed and used for programmatic analysis.
Using sevenlayers Nmap - xml2csv Tool
The sevenlayers Nmap - xml2csv tool converts Nmap XML output directly to CSV files. It streamlines data organization by ignoring hosts that are down and ports that are not open, focusing only on relevant, actionable data.
Converting XML with xml2csv.py Script
The xml2csv.py script available from NetsecExplained converts Nmap XML output to CSV. The script takes an XML output file as input and generates a CSV file. Similar to the sevenlayers tool, it can ignore non-essential data such as down hosts and closed ports, ensuring a clean and efficient CSV export.
Steps to Export Nmap Data to CSV
1. Run an Nmap scan and save the output in XML format.
2. Use either the sevenlayers Nmap - xml2csv tool or the xml2csv.py script.
3. Follow the tool or script execution instructions to generate your CSV file.
4. Open the generated CSV file using any spreadsheet software for analysis.
By following these methods, you can effectively export your Nmap scan results to CSV format, facilitating better data management and analysis.
Nmap Use Cases
Scan a Hostname
One common use case for Nmap involves scanning a hostname. This helps network administrators gather critical details about a specific host. By sending packets to the host and analyzing the responses, valuable information regarding the host's network and services can be collected.
Scan Multiple Hosts Listed in a File
Nmap is highly useful for scanning multiple hosts listed in a hosts.txt file. This feature enables administrators to efficiently manage and monitor large networks. Batch processing of host scans can unveil insights about network stability and security without manual input for each host.
Identify Host Operating Systems
Nmap can be used to identify a host's operating system, aiding in the inventory process. It allows for the automatic detection of OS types on devices, which helps in managing system updates and ensuring compatibility within the network.
Firewall and Port Analysis
Understanding security concerns by checking if a remote host has a firewall enabled and which ports are filtered is a critical use case for Nmap. This functionality assists in identifying potential security loopholes and fortifying network defenses against unauthorized access.
Analyze Open Ports
Nmap enables the analysis of open ports on a host to identify weak points. By scanning and reporting on available ports, administrators can pinpoint vulnerable services that need patches or stronger security measures.
Perform Stealth Scans
Performing a stealth scan for TCP information is a significant Nmap use case. This ensures more discreet network analysis without alerting the scanning process to potential intruders, aiding in covert security monitoring and penetration testing.
Penetration Testing
Nmap is extensively used in penetration testing to scan for open ports and gather network information. It simplifies detecting vulnerabilities and diagramming a target's network, essential for developing robust security strategies.
Network Mapping and Inventory
Nmap's flexibility and ability to work in customized environments make it an exceptional tool for network mapping and inventory. It can uncover unknown information, such as shadow IT, ensuring comprehensive network visibility and control.
Why Choose Sourcetable Over Nmap?
Sourcetable offers a unique approach to data management by collecting all your data in one place from various data sources. This streamlined solution allows you to query and manipulate your data through a familiar, spreadsheet-like interface.
Unlike Nmap, which specializes in network scanning and security auditing, Sourcetable excels in real-time data querying and manipulation. This makes it ideal for businesses that need to handle large datasets efficiently and require real-time insights.
For professionals who prioritize data accessibility and ease of use, Sourcetable provides a powerful alternative. The ability to extract and work with data effortlessly within a unified platform can significantly boost productivity and data accuracy.
Overall, if your focus is on simplifying data integration and enhancing real-time data analysis capabilities, Sourcetable is the superior choice compared to Nmap.
Frequently Asked Questions
What tool can be used to convert Nmap XML output to CSV?
The sevenlayers Nmap - xml2csv tool can be used to convert Nmap XML output to a CSV file.
Does the xml2csv tool account for hosts that are down or ports that are not open?
Yes, the xml2csv tool ignores hosts that are down and ports that are not open.
How do you execute the script from NetsecExplained to convert Nmap output to CSV?
You can use the command `python3 xml2csv.py -f nmap_scan.xml -csv nmap_scan.csv` to convert Nmap XML output to CSV.
Can Nmap output in formats other than XML?
Yes, Nmap offers several output formats including interactive output, normal output, XML, grepable output, and script kiddie output.
What are some benefits of using Nmap's XML output?
Nmap's XML output can be easily parsed by programs, converted to HTML, imported into databases, and used by Nmap graphical user interfaces.
Conclusion
Exporting data from Nmap to CSV is an essential skill for efficient data analysis. By following the steps outlined, you can seamlessly convert and utilize your data in various applications.
Make sure to validate the exported CSV files for accuracy before analysis. This ensures that the data is correctly formatted and ready for further processing or importing into other tools.
Sign up for Sourcetable to analyze your exported CSV data with AI in a simple to use spreadsheet.