Export Nessus Scan Results to CSV
Introduction
Exporting Nessus scan results to CSV format is essential for efficient data analysis and reporting. In this guide, you'll learn step-by-step how to export your Nessus scan results to a CSV file.
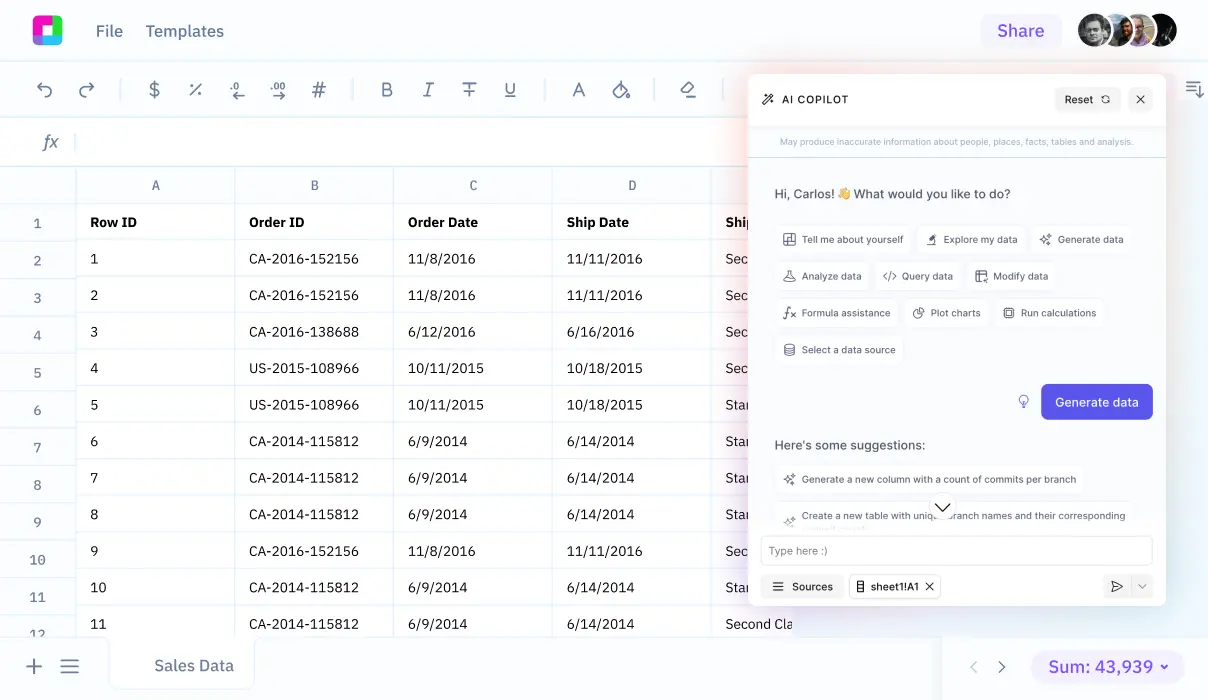
We'll also explore how Sourcetable lets you analyze your exported data with AI in a simple to use spreadsheet.
Exporting Nessus Scan Results to CSV Format
Prerequisites
To export Nessus scan results to CSV format, you need to install Cygwin along with the xsltproc libraries. These tools are necessary for parsing the .nessus file into a .csv file effectively.
Downloading Cygwin and xsltproc Libraries
First, download Cygwin from its official website. During the installation, ensure you include the xsltproc libraries. These libraries are essential for converting the .nessus file format.
Parsing .nessus Files
Once you have Cygwin and xsltproc installed, use xsltproc to parse the .nessus file. This process will convert your Nessus scan data into a .csv file, making it easier to manipulate and analyze your scan results.
Saving as .xlsx
To preserve any changes made to the CSV file, save it as an .xlsx file. This step ensures compatibility with most spreadsheet software, allowing for easier data handling and visualization.
Alternative Methods
For those using tenable.io, while most reporting is PDF-based, you can still access CSV reports. If the direct option is unavailable, consider using the API to generate a CSV report of vulnerabilities.
How to Export Your Data to CSV Format from Nessus Scan Results
Exporting Directly from the Nessus Interface
To export your Nessus scan results directly from the Nessus interface, first log into your Nessus Professional account. Choose the specific scan you wish to export and click on the Export button located at the top-right corner of your screen. From the export options, select CSV format and ensure you include all available columns. Next, click on Generate Report. The report file will be downloaded to your device as a CSV file.
Using Cygwin and xsltproc Libraries
If you prefer using Cygwin, start by downloading Cygwin with the xsltproc libraries. These libraries are necessary to parse the .nessus file into a .csv file. Use xsltproc to perform the parsing. Once you have the CSV file, you may want to save it as an .xlsx file in order to make and save any changes easily.
Opening and Customizing Your CSV Report
After exporting your scan results, open the CSV file in Excel. A dialog box will appear offering various options to customize your report. Ensure you select the relevant vulnerabilities you need to act on. The CSV file will include columns such as 'Synopsis', 'Description', and 'Solution', providing comprehensive details on the vulnerabilities identified.
Additional Tools for Exporting Data
For advanced users, there are tools available to further process and analyze Nessus scan results. One such tool allows exporting Nessus results into a database, which can facilitate easy analysis and extraction of statistics. This can be particularly useful for generating detailed insights and reports from your scan data.
Nessus Scan Results Use Cases
Asset Discovery
Nessus scan results are instrumental for asset discovery, providing detailed insights into the presence and status of network devices. Accurate asset discovery aids in creating comprehensive inventories and securing all connected devices.
Vulnerability Assessment
Utilizing Nessus scan results for vulnerability assessment helps organizations identify and prioritize security flaws. This process is crucial in safeguarding infrastructures and ensuring remediation efforts are effectively targeted.
Penetration Testing Reconnaissance
Before conducting breach simulations, network penetration testers leverage Nessus scan results to identify potential vulnerabilities. This preliminary reconnaissance is vital for informed and successful penetration testing.
Compliance Auditing
Organizations use Nessus scan results for auditing security frameworks and regulatory standards. This practice ensures compliance with industry regulations and helps maintain a strong security posture.
Threat Hunting with YARA
Threat hunters utilize Nessus scan results combined with YARA rules to identify and investigate potential threats. This integration enhances the capability to detect suspicious activities and mitigate risks promptly.
Active Directory Checks
Nessus scan results are essential for conducting thorough Active Directory checks. By analyzing these results, administrators can identify and rectify misconfigurations, bolstering the security of directory services.
Cloud Asset Auditing
Audit reports generated from Nessus scan results provide critical information about cloud assets. This auditing process helps organizations secure cloud environments and detect vulnerabilities specific to cloud infrastructures.
Network Infrastructure Audits
Nessus scan results enable comprehensive audits of network infrastructures and database configurations. This approach helps detect and resolve issues, ensuring the operational security of essential hardware and software components.
Why Sourcetable is an Excellent Alternative for Nessus Scan Results
Sourcetable offers an efficient way to collect all your data from various sources in one place. By integrating your Nessus scan results into Sourcetable, you gain access to real-time data queries using a familiar spreadsheet-like interface.
Unlike traditional methods, Sourcetable simplifies the process of data manipulation and analysis. This enables faster, more efficient handling of Nessus scan results, enhancing your ability to interpret and act on vulnerability data.
Utilize Sourcetable to centralize your database, breaking down data silos. This real-time access to critical Nessus scan results helps you stay ahead of security threats and maintain robust system integrity.
Frequently Asked Questions
Can Nessus scan results be exported to CSV?
Yes, Nessus scan results can be exported to CSV.
What tools are required to convert Nessus scan results to CSV?
Cygwin and the xsltproc libraries are required to convert Nessus scan results to CSV.
How does xsltproc work with Nessus files?
xsltproc takes .nessus files as input and converts them to CSV files.
Is it necessary to save the exported CSV file in a different format?
Yes, you must save the CSV file as an .xlsx file to save changes.
What is Cygwin used for in the process of exporting Nessus scan results to CSV?
Cygwin provides a Linux-like environment on Windows, required to run xsltproc for converting Nessus scan results to CSV.
Conclusion
Exporting Nessus scan results to CSV format is a straightforward process that facilitates detailed analysis and reporting. This guide has outlined the necessary steps to ensure your data is efficiently transferred.
Make sure to verify the export to maintain data integrity and reliability. Consistently updating and exporting your scans will lead to more comprehensive security assessments.
Sign up for Sourcetable to analyze your exported CSV data with AI in a simple-to-use spreadsheet.