Export Fortigate Configuration to CSV
Introduction
Exporting data from FortiGate configuration to a CSV file can streamline your network management and analysis processes. This can help in creating backups, performing audits, and migrating settings across different devices.
In this guide, we'll walk you through the necessary steps to export your FortiGate configuration to a CSV file efficiently. You'll learn how to leverage built-in tools and commands for a smooth export process.
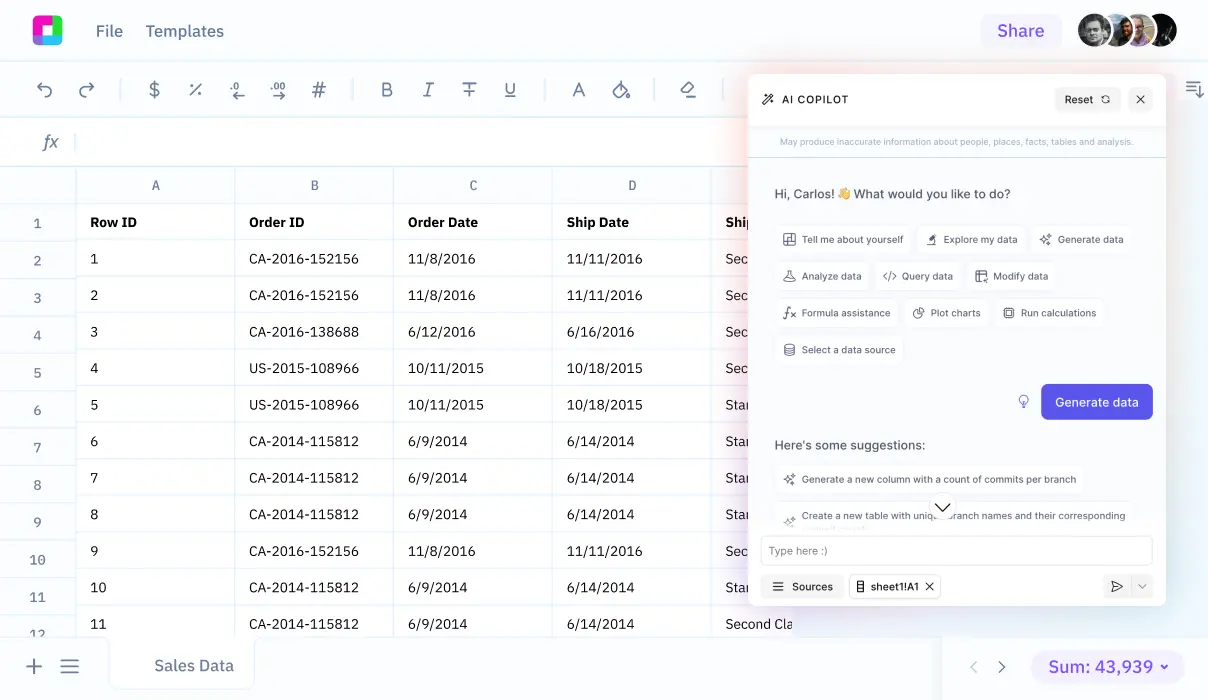
Furthermore, we'll explore how Sourcetable lets you analyze your exported data with AI in a simple to use spreadsheet.
Exporting FortiGate Configuration to CSV Format
Overview
Exporting FortiGate configuration data to CSV format is essential for backup, analysis, and migration purposes. This guide provides detailed steps on how to perform the export using FortiGate's various capabilities and tools.
Exporting Firewall Policy List
Starting from version 7.0.1, FortiGate allows users to export the current view of the firewall policy list to CSV format. To export the firewall policy list, navigate to Policy & Objects > Firewall Policy. In the toolbar above the list, click Export and select CSV. The file will be automatically downloaded to your local machine.
Script-Based Export with fgpoliciestocsv.py
For more advanced exporting needs, such as extracting IPv4 policies, the script fgpoliciestocsv.py can be utilized. This script must be run on a Unix or Linux environment. Begin by ensuring your FortiGate configuration file is in the standard format, e.g., 'Fortinet_2019121....conf'. Use the command ‘fgpoliciestocsv.py -i [cfg file name].cfg’ to run the script. The output will be a CSV file named ‘policies-out.csv’.
Moving and Converting the CSV File
Once the CSV file is generated, use WinSCP to transfer the file to a Windows environment if necessary. Open the file in Excel. To convert the data to columns, use Excel's 'Text to Columns' feature, selecting Delimited options 'Tab' and 'Semicolon'. This ensures that the data is properly formatted within Excel for further analysis or use.
Using FortiManager for Export
In scenarios where you need to extract IPv4 policies directly from FortiGate to CSV files, you should utilize FortiManager. FortiManager is specifically designed to handle such tasks efficiently, complementing the capabilities provided by the fgpoliciestocsv.py script.
By following these steps, you can effectively export your FortiGate configuration data to CSV format, ensuring that your network policies and settings are securely backed up and easily accessible for analysis and future use.
Exporting Your FortiGate Configuration to CSV Format
Export Firewall Policy List to CSV
FortiGate allows exporting the current view of the Firewall Policy list to CSV. This feature is available starting from version 7.0.1. To export, navigate to Policy & Objects > Firewall Policy. In the toolbar above the list, click Export and select CSV. The file will be automatically downloaded.
Export IPv4 Policies to CSV Using Script
While FortiGate cannot directly extract IPv4 policies to CSV files, the fgpoliciestocsv.py script can be utilized for this purpose. Download the script from here and run it on a Unix or Linux system. The generated CSV file can be opened using Excel.
Downloading FortiGate Configuration File via GUI
To download the FortiGate configuration file, go to Admin > Configuration > Backup. Select Local PC in the Backup to option and click OK. The configuration backup can be saved in either FortiOS or YAML format, with FortiOS format generally recommended.
Export Device Lists to CSV Using FortiManager
To export device lists from FortiManager, select Table View from the Device Manager > Device & Groups toolbar. Choose a device group under Managed Devices, then from the More menu, select Export Device List. In the Export to CSV dialog box, you can change the file name and select which columns to include, along with options to include information on FortiAP, FortiSwitch, and FortiExtender.
FortiGate Configuration Use Cases
1. Management Access Set Up
FortiGate can be configured to allow management access, providing administrators with secured and controlled entry for configuration and monitoring. This setup ensures that only authorized users have access to management interfaces, using features such as the FortiGate REST API and TACACS+ VSA attributes for enhanced security and flexibility.
2. Implementing Firewall Policies
Configuring a firewall policy on FortiGate allows for effective traffic management and enhanced security. This can involve setting rules for traffic based on criteria such as IP addresses and protocols, ensuring the network is safeguarded against unauthorized access and threats. Examples include using wildcard and geography-based addresses in policies.
3. Advanced Routing Configuration
FortiGate supports both static and dynamic routing, enabling efficient and adaptive traffic handling across the network. Configurations can include setting up static routes for known destinations or using dynamic routing protocols such as BGP for scalable and responsive routing solutions. These routing configurations ensure optimal path selection and network performance.
4. Configuring VPN Overlays
VPN overlays on FortiGate can be configured to secure data transmission across public networks. This includes setting up IPsec VPNs and using advanced VPN technologies like ADVPN for enhanced security and flexibility. VPN overlays are crucial for secure and reliable remote access and connectivity between distributed network nodes.
5. Utilizing SD-WAN for Optimized Traffic
FortiGate can be configured to use SD-WAN, optimizing traffic routing and improving network performance. SD-WAN configurations enable intelligent path control, ensuring application traffic is routed over the best available path based on performance metrics. This maximizes bandwidth efficiency and improves user experience.
6. Deploying DHCP Servers and Relays
Deploying DHCP servers and relays on FortiGate simplifies IP address management within the network. Configuration examples include setting up FortiGate as a DHCP server to dynamically assign IP addresses to devices or configuring it as a relay to forward DHCP requests. This assist in maintaining an organized and efficient network environment.
7. Setting Up Proxies for Traffic Inspection
FortiGate supports both explicit and transparent proxy configurations, allowing in-depth traffic inspection and filtering. Proxies can be used to enforce security policies and content filtering, manage bandwidth usage, and provide detailed analytics on traffic patterns. This enhances network security and optimizes resource utilization.
8. Enhancements with WAN Optimization
WAN optimization configurations on FortiGate improve data transfer efficiencies over WAN connections. Examples include manual configuration, active-passive WAN optimization, and secure tunneling. These configurations reduce latency, increase throughput, and ensure secure and reliable communication across wide-area networks.
Why Sourcetable is an Alternative for FortiGate Configuration
Sourcetable offers a comprehensive solution for managing and querying data, making it a versatile alternative to FortiGate configuration. Unlike FortiGate, which focuses on security configurations, Sourcetable allows you to collect data from multiple sources into a single interface.
With Sourcetable, you can query your database in real-time. This functionality is crucial for businesses that need immediate access to data without the complexities of network security configuration. It streamlines data manipulation, offering a spreadsheet-like interface that is intuitive and user-friendly.
Sourcetable excels in data integration and manipulation, providing a seamless experience absent in traditional security-focused configurations. For organizations looking to simplify their data operations, Sourcetable is an invaluable tool.
By using a familiar spreadsheet interface, Sourcetable eliminates the steep learning curve associated with FortiGate's configuration environment. It allows for real-time data access and manipulation, making your data management process more efficient and effective.
Frequently Asked Questions
How can I export the firewall policy list to CSV using the FortiGate GUI?
To export the firewall policy list to a CSV file, go to Policy & Objects > Firewall Policy. In the toolbar above the list, click Export and select CSV. The file is automatically downloaded.
Which FortiGate versions support exporting the configuration to CSV?
The ability to export the firewall policy list to CSV was added in FortiGate version 7.0.1 and is supported in versions 7.0.1 and above.
What are the steps to export FortiGate configuration to CSV using a script?
To export FortiGate configuration to CSV using the fgpoliciestocsv.py script, follow these steps: 1) Download the script from https://github.com/maaaaz/fgpoliciestocsv/find/master?q=, 2) Export the configuration of the FortiGate, 3) Search 'config firewall policy' in the configuration file, 4) Copy and paste IPv4 policies to a cfg file named 'fgfw.cfg', 5) Upload the fgfw.cfg and fgpoliciestocsv.py files to a Unix or Linux based OS, 6) Execute the command 'fgpoliciestocsv.py -i fgfw.cfg', 7) Use WinSCP to move the resulting 'policies-out.csv' file to a Windows OS, 8) Open the file in Excel and convert text to columns, setting the delimiter to Tab and Semicolon.
Can FortiGate export configurations to CSV using the CLI?
Yes, FortiGate configurations can be exported to CSV using the CLI in versions 7.0.1 and above.
What tools are required to use the fgpoliciestocsv.py script?
The script fgpoliciestocsv.py requires a Unix or Linux based OS, WinSCP, and Excel to open the CSV file. Additionally, you need to set the delimiter to Tab and Semicolon in Excel.
Conclusion
Exporting data from FortiGate configuration to CSV format is a straightforward process when following the steps outlined in this guide. This allows for easier data management and analysis outside the FortiGate environment.
Once you have your data in CSV format, you can leverage powerful tools to gain deeper insights. Sign up for Sourcetable to analyze your exported CSV data with AI in a simple-to-use spreadsheet.