Export Folder Permissions to CSV
Introduction
Exporting folder permissions data to CSV is an essential task for administrators managing user access rights. A CSV file provides a straightforward format for storing and sharing permission information efficiently.
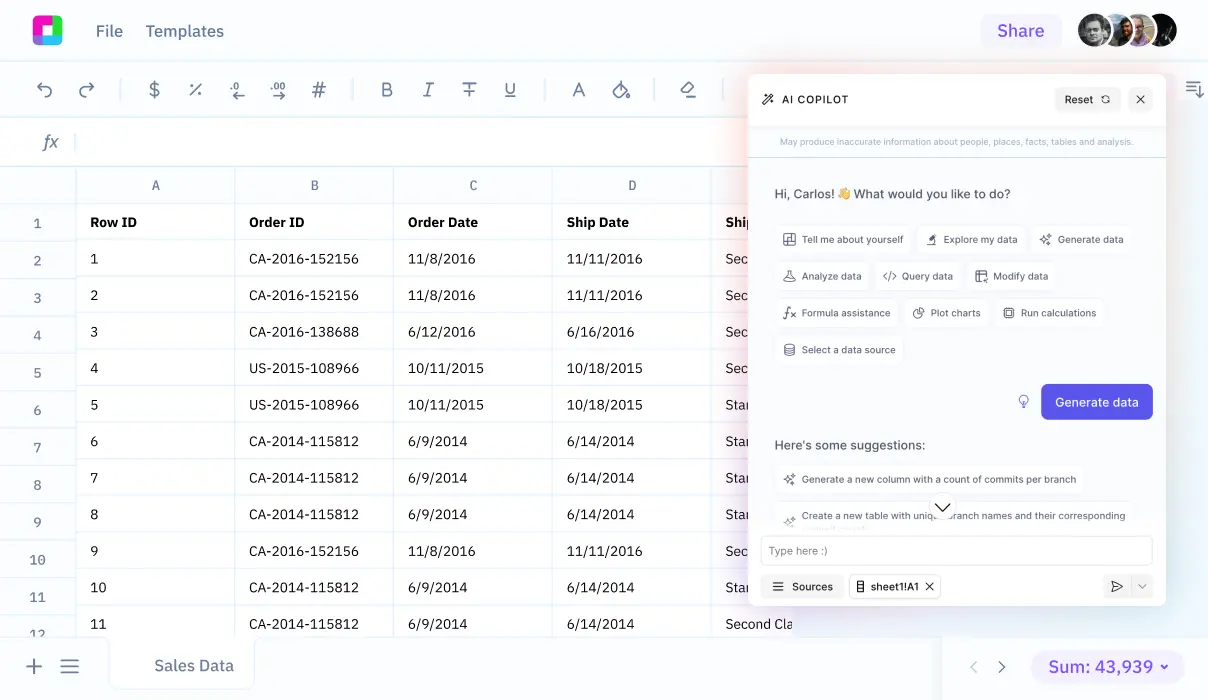
This guide will walk you through the steps necessary to export your folder permissions data to a CSV file. You will also learn how Sourcetable allows you to analyze your exported data with AI in a simple to use spreadsheet.
Exporting Folder Permissions to CSV Format
Exporting folder permissions to CSV is essential for audit checks and permissions reviews. Utilizing PowerShell, this process can be efficient and straightforward. Below are the steps and commands necessary to achieve this.
Prerequisites
Before proceeding, ensure you have PowerShell installed on your system. PowerShell scripts are required to export folder permissions to CSV format.
Step 1: Using Get-ChildItem to List Folders
Start by using the Get-ChildItem command to list the folders you want to export permissions for. This command retrieves the folder structure and can be customized with flags such as -recurse and -force for in-depth searches.
Step 2: Retrieving ACLs with Get-Acl
Once the folders are listed, use the Get-Acl command to get the Access Control Lists (ACLs) for each folder. This command collects the necessary permissions data for each directory.
Step 3: Adding Folder Properties
To include folder-specific information in your export, use the Add-Member command. This command appends the Folder property to each ACL entry, providing clarity on which permissions correspond to which directories.
Step 4: Converting Paths
For a standardized format, employ the Convert-Path command. This ensures that all folder paths are correctly formatted before exporting.
Step 5: Exporting to CSV
After preparing the data, use the Export-Csv command to create the CSV file. This command converts the collected ACL information into the CSV format, which can be reviewed in Excel or any other CSV-compatible application.
Tips for Efficient Export
To only include folders in your permissions export, use the -Directory flag with the Get-ChildItem command. Including the Owner field can be done using Select-Object with the Owner property. To simplify smaller exports or work on older Windows versions, consider using cacls, although it is an outdated method.
Reviewing Permissions in Excel
Once the CSV file is generated, open it in Excel for a clear overview of your folder permissions. Reviewing permissions this way can help identify overexposed permissions and improve security.
How to Export Folder Permissions to CSV
Exporting folder permissions to a CSV file can be efficiently done using PowerShell. This process helps in reviewing and auditing access controls and identifying overexposed permissions in a structured format.
Step-by-Step Guide
First, utilize the PowerShell command Get-Acl to retrieve the Access Control List (ACL) for your folder. This command is essential for gathering all necessary permission details.
To capture permissions of each folder and sub-folder, use the Get-ChildItem cmdlet. This cmdlet allows you to list items in one or more specified locations.
You can add custom properties to the retrieved data using the Add-Member cmdlet. This step is crucial for including additional attributes, such as folder paths, in your CSV file.
Use the Convert-Path cmdlet to convert the folder paths to a more readable and standardized format. This ensures consistency in the exported data.
To control the output, use the Select cmdlet to specify which properties should be included in the final export. This allows for a cleaner and more relevant CSV file.
Finally, export the ACL information to a CSV file using the Export-Csv cmdlet. Include the -NoTypeInformation switch to prevent type information from being added to the CSV file, keeping it clean and readable.
Example Script
Here is an example PowerShell script that puts it all together:
Review in Excel
Once exported, open the CSV file in Microsoft Excel for further review. Excel provides tools for sorting, filtering, and analyzing the data, making it easier to identify potential security risks.
By following these steps, you can efficiently export and review folder permissions, ensuring your data access controls are properly managed.
Folder Permissions Use Cases
Granting Specific User Permissions
A user can be granted permission to view, edit, or create objects within a folder. Specific permissions such as Read, Write, and Modify can be set based on individual or group needs, reducing user error and enhancing security.
Reducing Data Breach Risks
Limiting the number of users with privileged credentials significantly reduces the risk of a data breach. By restricting user permissions, it becomes more difficult for unauthorized access, protecting sensitive information from hackers and automated attacks.
Combining NTFS and Share Permissions
NTFS and share permissions combine to determine access levels to files and folders. This approach leverages the most restrictive permissions, ensuring that any security lapses are minimized. Explicit permissions take precedence, providing granular control over access rights.
Managing Application Access
Applications can be configured to read and write to specific folders without granting users the same permissions. By utilizing local service accounts, applications can manage folder access securely, ensuring users do not have unauthorized access to sensitive data.
Creating and Editing Subfolders
Users can be granted permission to create and edit subfolders within a parent folder. This flexibility allows for better organization of data while maintaining control over who can modify the folder structure, preventing accidental or malicious changes.
Encrypting and Hiding Folders
Applications can encrypt files and hide folders to prevent unauthorized user access. This method enhances data security by ensuring that only authorized applications can access or modify the content, further protecting against data breaches and user errors.
Why Choose Sourcetable Over Folder Permissions
Sourcetable offers a centralized solution for data management, unlike traditional folder permissions which fragment data across directories. By consolidating all data sources into a single spreadsheet-like interface, Sourcetable eliminates the need for managing multiple folder permissions, streamlining access and analysis.
With Sourcetable, you gain real-time access to your database, allowing for immediate querying and data manipulation. In contrast, folder permissions can delay data retrieval and hinder efficient workflows. Sourcetable’s approach ensures timely insights and faster decision-making.
Folder permissions often require intricate management to ensure data security. Sourcetable simplifies this by providing an intuitive platform where access control is inherent and easier to administrate, reducing complexity and the risk of errors.
Sourcetable's unified interface enhances collaboration by enabling users to work on the same dataset simultaneously. Folder permissions can create silos and limit collaborative efforts. With Sourcetable, teams can seamlessly share and analyze data together, driving better outcomes.
Frequently Asked Questions
What is the primary method to export folder permissions to a CSV file?
Powershell is the primary way to export folder permissions to a CSV file.
What command can be used in Powershell to get folder permissions?
The command Get-ChildItem can be used to get the folders, and get-acl can be used to get the folder permissions.
Can I use AccessEnum.exe to export folder permissions to CSV?
Yes, AccessEnum.exe is a SysInternals tool that creates a TXT file, which can be imported into Excel and saved as a CSV.
Is there an alternative to using Powershell for exporting folder permissions?
Yes, the command cacls can be used from the command line, although it has limitations, and the created file can be imported into Excel.
How can I ensure only folders are listed when exporting permissions using Powershell?
You can use the -Directory flag with Get-ChildItem to ensure only folders are listed.
Conclusion
Exporting folder permissions to CSV is a straightforward process that ensures you have clear, structured data for further analysis.
By following the steps provided, you can efficiently handle your folder permissions data to meet your operational needs.
Sign up for Sourcetable to analyze your exported CSV data with AI in a simple-to-use spreadsheet.