Export Checkpoint Logs to CSV
Introduction
Exporting Checkpoint logs to CSV is a crucial task for data analysis and archiving. This guide provides a step-by-step approach to effectively exporting Checkpoint logs.
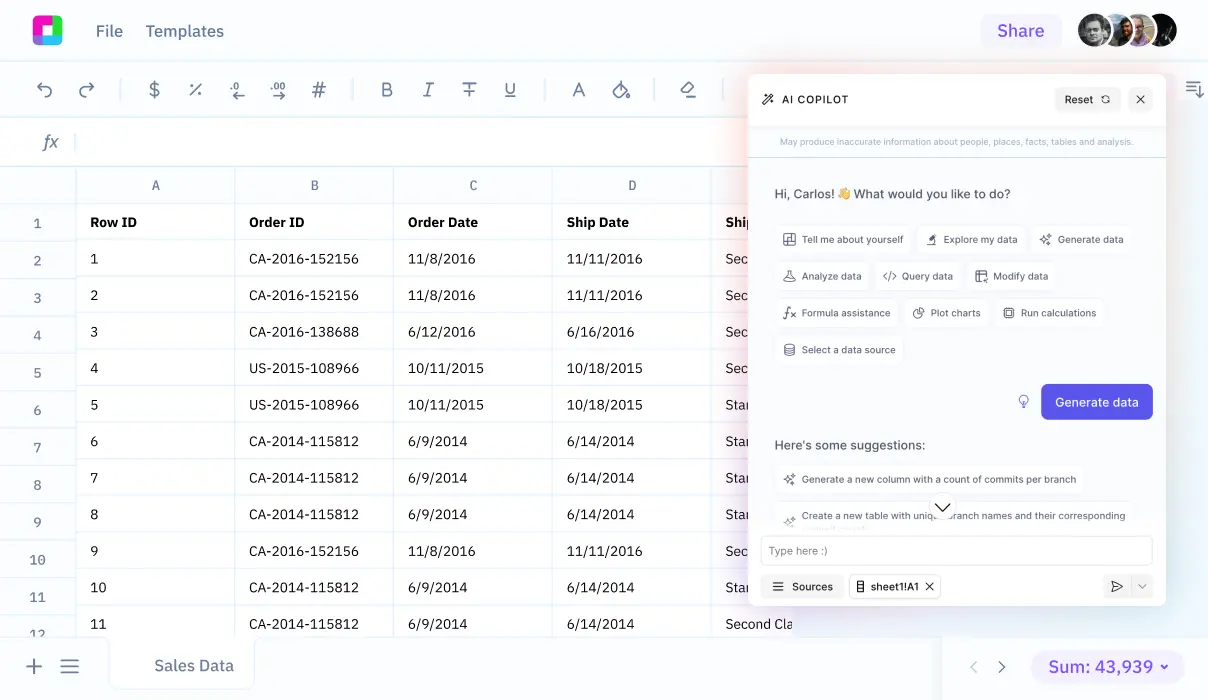
We will detail the necessary procedures and commands to transform your data into a CSV format. Additionally, we'll explore how Sourcetable lets you analyze your exported data with AI in a simple to use spreadsheet.
How to Export Your Data to CSV Format from Checkpoint Logs
Introduction to Exporting Checkpoint Logs
Checkpoint's SmartView allows users to export logs to CSV format directly from the Logs & Monitor pane. This functionality is essential for those who need to analyze log data in spreadsheet software or import it into other tools that accept CSV files.
Exporting Logs Using SmartView
To export logs using SmartView, navigate to the Logs & Monitor pane. From there, you can export logs for either 7 days or 30 days. SmartView supports exporting up to 1 million log entries, but keep in mind that the logs will be exported as multiple CSV files.
Process Overview
Exporting Checkpoint logs via SmartView is straightforward. Once you initiate the export, you will be prompted to save the CSV file to the machine running the browser with SmartView. Note that the logs in the display buffer and any applied filters will influence the data included in the CSV.
Potential Issues and Limitations
Be aware of several potential issues: the export process may fail, it might succeed but not export all logs, or it may only export logs from the last 30 minutes. Ensure to review the exported data for completeness.
Alternative Methods: Log Exporter and REST API
Beyond SmartView, you can use Log Exporter to export logs to a syslog server or third-party SIEM. Alternatively, the REST API can be utilized to export logs in a single CSV file, offering a different approach for data extraction needs.
How to Export Checkpoint Logs to CSV Format
Using SmartView Web Portal
To export Checkpoint logs to CSV format, you can use the SmartView web portal. This tool supports exporting logs from the Logs & Monitor pane and allows for downloads in both CSV and PDF formats. The exported logs can be filtered, scrolled through, and downloaded directly on the machine running the browser with SmartView.
SmartView can export logs for a duration of 7 or 30 days. For extensive log data, SmartView supports exporting up to 1 million logs. The logs from a display buffer are available for export, and the log entries will be in ASCII text format.
Using Legacy R80 SmartView Tracker
If the log files are too large to be opened in the SmartView web portal, you can use the legacy R80 SmartView Tracker application. This application also supports exporting logs in CSV or PDF format and is a reliable alternative for handling large log files.
Exporting Logs via Command Line
Checkpoint logs can also be exported using the command line. Use the fwm logexport command to export logs as needed. This method is practical for users who prefer command-line operations or need to automate the export process.
Additional Methods
Log Exporter can be used to export logs to a syslog server or third-party SIEM. Additionally, log queries can be performed via REST API starting from R80.40 JHF 78, providing further flexibility in handling and exporting log data.
Each of these methods offers a customizable approach to exporting Checkpoint logs, ensuring that your logging and data analysis needs are adequately met.
Use Cases Unlocked by Checkpoint Logs
Monitoring and Responding to Security Threats
Checkpoint logs are essential for both monitoring and responding to security threats. They provide real-time threat analysis and allow for immediate response to mitigate risks. Using these logs ensures that businesses can promptly identify and address potential security breaches, improving overall security posture.
Gaining Network Insights
By leveraging Checkpoint logs, organizations can gain critical network intelligence. These logs offer insights into network usage, identify applications and widgets in use, and help understand bandwidth consumption. This information is vital for optimizing network performance and planning future capacity.
Troubleshooting and System Performance
Checkpoint logs are invaluable for troubleshooting network issues. They help pinpoint the root causes of problems and suggest remedial actions. Additionally, Checkpoint's GenAI Security can handle high log rates, ensuring system performance remains optimal even under heavy logging activities.
Risk Assessment and Compliance Reporting
Checkpoint logs play a significant role in business risk assessment by providing detailed information on security breaches and attempted attacks. Regular analysis of these logs helps in identifying vulnerabilities and ensuring compliance with industry standards.
Application Control and Policy Management
Integrated within Check Point NGFW, Application Control uses Checkpoint logs to manage and enforce granular policies based on user behaviors. This feature identifies, blocks, or limits the usage of applications, thereby protecting the network against threats and malware effectively.
Advanced Threat Detection
Checkpoint logs offer advanced threat detection capabilities by analyzing logs for patterns indicating attacks like viruses, trojans, and denial-of-service attempts. This proactive approach helps in early detection and prevention of complex threats, safeguarding the network infrastructure.
Why Choose Sourcetable Over Checkpoint Logs?
Sourcetable is a spreadsheet solution that integrates data from multiple sources into one unified interface. It allows users to query data in real-time and perform analysis using a familiar spreadsheet format. This feature provides a streamlined and efficient alternative to Checkpoint logs.
Using Sourcetable, you can access and manipulate your data instantly, without the need to navigate complex logging systems. This real-time data access ensures you have the most up-to-date information at your fingertips, allowing for more accurate and timely decision-making.
Sourcetable simplifies data handling with its easy-to-use spreadsheet-like interface. You can perform all your data queries and analyses in one place, reducing the need to switch between different applications or logging systems. This consolidation of data management tools enhances productivity and efficiency.
For businesses looking to improve their data operations, Sourcetable offers a powerful, user-friendly, and integrated solution that outperforms traditional Checkpoint logs. Experience seamless data integration and real-time insights with Sourcetable.
Frequently Asked Questions
How can I export Checkpoint logs to a CSV file?
To export Checkpoint logs to a CSV file, you can use SmartView. Navigate to the Logs & Monitor pane, and the export will be available there. Once the export is complete, you can download the CSV file.
What tools are available for exporting Checkpoint logs to CSV?
You can use SmartView or Log Exporter to export Checkpoint logs to a CSV file. SmartView can export directly from the Logs & Monitor pane, while Log Exporter can export to a syslog server, third party SIEM, or via REST API.
Is there a limit on the number of lines in the exported CSV from Checkpoint logs?
Yes, the exported logs in CSV format can be up to 1 million lines when using SmartView.
Where are the exported CSV files stored when using SmartView?
The exported CSV files are stored on the machine running SmartView, and they can be downloaded after the export process is complete.
What is required to use Log Exporter for exporting Checkpoint logs to CSV?
Log Exporter, available from R80.40 JHF 78, is required to export Checkpoint logs to CSV. It can export logs to a syslog server, third party SIEM, or via REST API.
Conclusion
Exporting Checkpoint logs to CSV is a straightforward process that can significantly aid in log analysis and data management. Following the proper steps ensures that the data is accurately converted and ready for further use.
Once you have your CSV file, you can leverage it for advanced analysis and reporting. Efficient data handling allows for better decision-making and security management.
Sign up for Sourcetable to analyze your exported CSV data with AI in a simple to use spreadsheet.