Export Checkpoint Firewall Rules to CSV
Introduction
Exporting data from Checkpoint Firewall Rules to CSV is an essential task for managing and analyzing firewall configurations efficiently. This process allows administrators to easily review, audit, and share firewall rules.
In this guide, we provide step-by-step instructions to help you export your Checkpoint Firewall Rules to a CSV file. You'll learn the prerequisites, necessary tools, and commands for a smooth export.
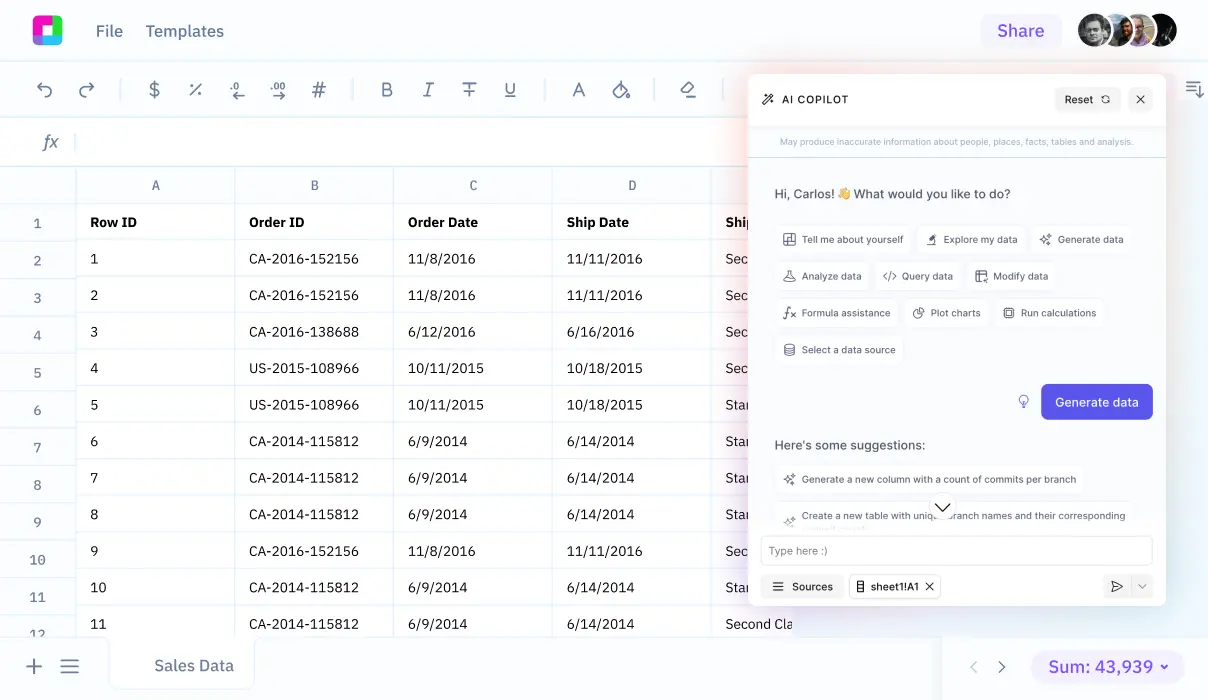
Finally, we will explore how Sourcetable lets you analyze your exported data with AI in a simple-to-use spreadsheet.
Exporting Checkpoint Firewall Rules to CSV
Overview
Exporting firewall rules from your Checkpoint Firewall to a CSV format can be done using various methods, including the GUI and command-line interface. This guide outlines the necessary steps to perform these exports efficiently.
Using SmartConsole GUI
To export a rulebase using the GUI, you can utilize the SmartConsole. Once you've launched SmartConsole, navigate to the rulebase you intend to export. The export option is accessible from the toolbar by selecting 'Action' followed by 'Export'. This method allows you to obtain the rulebase in a CSV format directly from the graphical interface.
Command-Line Interface
If you prefer using the command-line interface, you can switch to expert mode on your Checkpoint Firewall. Use the command "mgmt_cli show packages" to display the firewall policies and NAT rules. For exporting, the "mgmt_cli export" command can be utilized, although it has a 500-line limit. To export more than 500 lines, append the "offset" parameter to fetch subsequent lines.
Verifying and Retrieving Exports
The output from command-line commands can be piped into "jq" to format the data fields as needed. You can also use the "pwd" command to verify where the exported configuration file is saved, usually in the user's home directory.
Saving Configuration Using Gaia OS
The Checkpoint Firewall runs on GAIA OS, which includes built-in commands like "clish -c 'show configuration' > my_config.txt" and "clish -s 'save configuration". These commands save the current configuration to a text file, which can be easily converted to CSV if required.
Benefits of Exporting Rules
Exporting firewall rules to CSV format is beneficial for sharing configurations with others, performing audits, and ensuring you have a backup of your current ruleset. Understanding and utilizing these methods provides flexibility and ensures that you can manage and secure your firewall efficiently.
How to Export Checkpoint Firewall Rules to CSV Format
Using SmartConsole GUI
Exporting a rulebase in CSV format is available directly from the SmartConsole GUI. Follow these steps:
Open SmartConsole and navigate to the rulebase you wish to export. From the rulebase's toolbar, select 'Action > Export'. The rulebase will be exported in CSV format.
Using CLI Commands
To export firewall policies and NAT rules using CLI commands, start by showing available packages with the command mgmt_cli show packages. For access rulebase, use mgmt_cli show access-rulebase name Network package <policy_name>. For NAT rulebase, use mgmt_cli show nat-rulebase package <policy_name>.
To export policies, use mgmt_cli export. Note that the export bar code has a maximum of 500 lines. To export more than 500 lines, use additional parameters. The output from mgmt_cli export can be parsed with jq and formatted as CSV.
Alternative Methods
You can also use Check Point's tool to export and import policies using Python or CSV. These tools offer flexibility and additional functionality for managing exports.
Exporting Security Policies to HTML and Excel
For exporting security policies to Excel, use Check Point's Show Package Tool to export your security policy to HTML. SSH into the export mode of your SmartCenter and run $MDS_FWDIR/scripts/web_api_show_package.sh -n 443 -c. Copy the resulting .tgz to your Admin PC and unarchive it.
Open the exported security policy in your web browser, use DOM inspect to save it into a new .html file, and remove unnecessary JavaScript with a text editor. Replace #!%!#. Open the .html file in a browser, copy all content, and paste it into an empty Excel sheet.
Use Cases for Checkpoint Firewall Rules
Securing Network Perimeters
Checkpoint Firewall Rules play a crucial role in protecting network perimeters. By controlling both incoming and outgoing traffic, they effectively prevent unauthorized access and safeguard the network's edge, ensuring only vetted entities can enter or exit the network environment.
Granular Traffic Control
Organizations can leverage Checkpoint Firewall Rules to deny inbound traffic by default and create exceptions for permitted types of traffic. This granular control allows administrators to permit necessary HTTPS and DNS traffic for web browsing while blocking unwanted protocols like ICMP to prevent network scanning and information leaks.
Remote Access Management
Checkpoint Firewall Rules provide flexible options for managing remote access. Companies may allow inbound SSH traffic to enable remote users to connect securely to corporate devices while blocking SSH traffic to prevent unauthorized access. This capability ensures secure remote operations without compromising security.
Automating Firewall Management
Using tools like Terraform, organizations can automate the configuration and ongoing maintenance of Checkpoint firewall settings. Terraform scripts can manage VPN interfaces, BGP routing setups, and ACL groups, streamlining operations and reducing the need for manual intervention.
Enhancing Security for Events and Corporations
Organizations like the Denver Broncos utilize Checkpoint technology to secure data, email, and wifi during events. This comprehensive security approach ensures that both employees and visitors operate within a protected environment, safeguarding sensitive information and communications.
Improving Visibility and Security Management
Entities such as the Council of Cádiz benefit from using Checkpoint Firewall Rules to gain visibility into network traffic and simplify security management. Consistent monitoring and management of security parameters help in anticipating and mitigating potential threats efficiently.
Securing Multi-Cloud Environments
Companies like Santillana Latam utilize Checkpoint Firewall Rules to secure their networks, multi-cloud environments, and endpoints. Enhanced visibility and proactive threat detection enable these organizations to maintain robust security postures across diverse IT infrastructures.
Protecting High-Performance Networks
Research networks such as those managed by SingAREN use Checkpoint Firewall Rules to safeguard high-performance infrastructures. By implementing robust firewall configurations, these networks ensure secure data transmission and reliable protection against potential cyber threats.
Why Choose Sourcetable Over Checkpoint Firewall Rules?
Sourcetable seamlessly integrates various data sources into a single spreadsheet, enabling real-time data querying and manipulation. This streamlined approach simplifies data management, making it an efficient alternative to Checkpoint Firewall Rules.
With Sourcetable's intuitive spreadsheet interface, users can easily access and organize data without needing complex configurations. This user-friendly experience improves productivity and reduces dependency on specialized IT support.
By consolidating data from multiple sources, Sourcetable enhances visibility and control, aiding in more effective decision-making. This holistic data view is a critical advantage over the traditional firewall configuration and management methods.
Frequently Asked Questions
How can I export Checkpoint Firewall rulebase to a CSV file using the GUI?
To export a rulebase using CSV format from the GUI, open SmartConsole and view the rulebase you wish to export. Then, select 'Action > Export' from the rulebase's toolbar.
Can I export firewall policies and NAT rules to CSV using the command line?
Yes, you can export firewall policies and NAT rules to CSV using the command line by using the mgmt_cli command with the appropriate parameters. The output can be formatted using jq.
What is the limit of records that can be exported to CSV in R80.x?
By default, R80.x limits the number of records exported to CSV to 217 in the current view. Scrolling down allows exporting more records.
Is it possible to export logs to CSV in R81?
Yes, logs can be exported to CSV in R81 using the SmartView web portal, with a limit of up to 1 million records.
Can Checkpoint Firewall rules be imported directly from a CSV?
No, while you can export rules to a CSV format, rules cannot be imported directly from a CSV.
Conclusion
Exporting Checkpoint Firewall Rules to CSV is a straightforward process that can enhance your data analysis capabilities. Following the necessary steps ensures your firewall rules are efficiently transferred for better insights.
Use the exported CSV file to dive deeper into your network security data. Sign up for Sourcetable to analyze your exported CSV data with AI in a simple-to-use spreadsheet.