Turn Security Chaos Into Clear Intelligence
Every security team knows the feeling: incident alerts flooding in, spreadsheets scattered across drives, and the constant pressure to make sense of it all. You're not just managing incidents—you're trying to spot patterns, measure response times, and prove your team's value to executives who speak in budgets, not breach statistics.
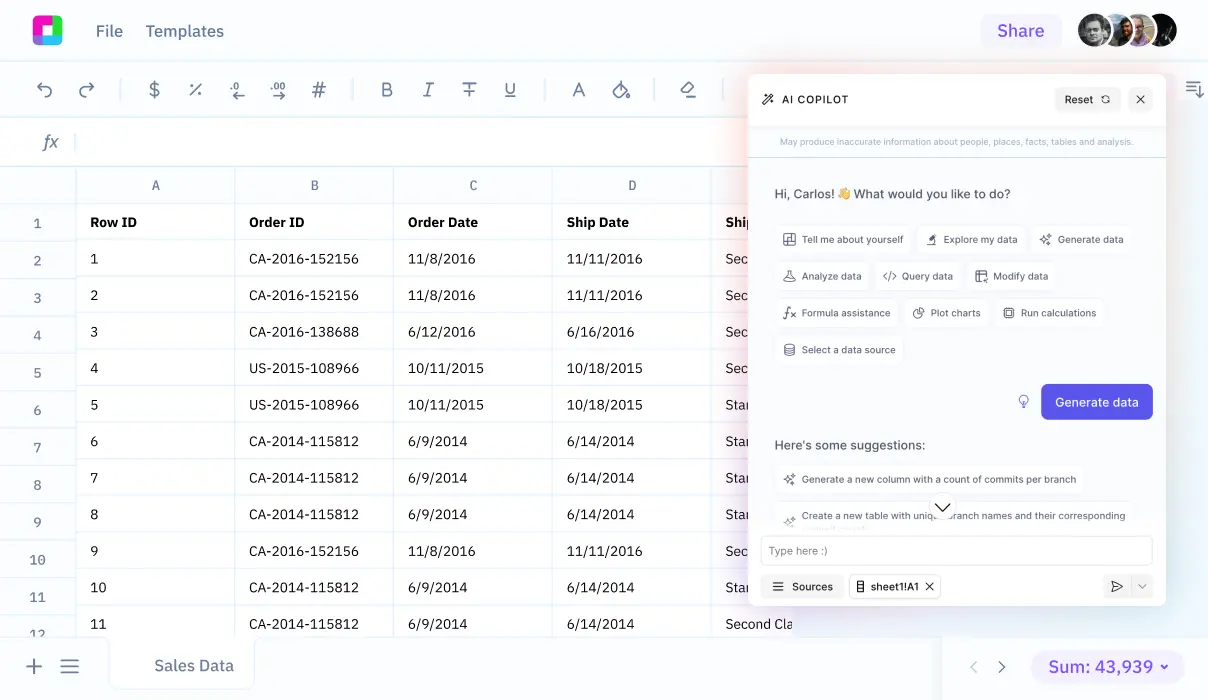
Security incident analysis shouldn't require a PhD in data science. With Sourcetable's AI-powered approach, you can analyze incident patterns, track response effectiveness, and generate executive-ready reports—all from the familiar interface of a spreadsheet.
Why Security Teams Choose Sourcetable
From SOC analysts to CISOs, security professionals use Sourcetable to transform incident data into actionable intelligence.
Automated Incident Correlation
AI automatically identifies patterns across incident types, attack vectors, and timeline data. Spot recurring threats before they become major breaches.
Response Time Analytics
Track mean time to detection (MTTD) and mean time to response (MTTR) across different incident categories. Identify bottlenecks and optimize your processes.
Executive Reporting
Generate board-ready reports with clear visualizations showing security posture improvements, incident trends, and ROI metrics.
Threat Intelligence Integration
Combine internal incident data with external threat feeds to build comprehensive risk profiles and predictive models.
Compliance Documentation
Automatically generate audit trails and compliance reports for frameworks like SOC 2, PCI DSS, and GDPR incident requirements.
Team Performance Metrics
Measure analyst productivity, identify training needs, and recognize top performers with detailed performance analytics.
Real-World Security Analysis Examples
See how security teams use Sourcetable to transform incident data into actionable insights.
Phishing Campaign Pattern Detection
A financial services company noticed suspicious email patterns but couldn't connect the dots across 200+ daily incidents. Using Sourcetable's AI analysis, they discovered a coordinated phishing campaign targeting specific departments, reduced similar incidents by 85%, and identified compromised accounts within hours instead of weeks.
Insider Threat Behavioral Analysis
A technology firm's SIEM generated thousands of user activity alerts monthly. By analyzing login patterns, file access times, and system behaviors in Sourcetable, they identified three high-risk users exhibiting unusual data access patterns, preventing potential intellectual property theft.
Ransomware Attack Timeline Reconstruction
After a ransomware incident, a healthcare organization needed to reconstruct the attack timeline for insurance claims and regulatory reporting. Sourcetable's analysis of log files, network traffic, and system events created a detailed forensic timeline, reducing investigation time from weeks to days.
Multi-Vector Attack Correlation
A retail company faced simultaneous DDoS attacks, credential stuffing attempts, and suspicious network scans. Sourcetable's correlation engine revealed these weren't separate incidents but a coordinated attack designed to mask a targeted data exfiltration attempt.
Security Investment ROI Analysis
A mid-sized company's CISO needed to justify budget increases to the board. By analyzing incident costs, response times, and prevention metrics in Sourcetable, they demonstrated that security investments reduced breach costs by 60% and improved detection times by 75%.
Your Security Analysis Workflow
From raw incident data to executive insights in four simple steps.
Import Incident Data
Connect your SIEM, ticketing systems, and log files directly to Sourcetable. Our AI automatically structures unformatted security data, saving hours of manual cleanup.
AI-Powered Pattern Recognition
Our intelligent algorithms analyze incident attributes, timelines, and relationships to identify hidden patterns, emerging threats, and response bottlenecks you might miss manually.
Interactive Analysis Dashboard
Explore your security data with dynamic charts, filters, and drill-down capabilities. Ask questions in plain English and get instant answers about your security posture.
Automated Reporting
Generate customized reports for different stakeholders—technical details for your team, executive summaries for leadership, and compliance documentation for auditors.
Essential Security Analyses You Can Perform
Incident Classification and Trending
Automatically categorize incidents by severity, attack vector, and affected systems. Track trends over time to identify whether your security posture is improving or if new threat patterns are emerging. Perfect for quarterly security reviews and trend reporting.
Response Time Analysis
Measure and optimize your incident response process. Analyze detection times, escalation patterns, and resolution speeds across different incident types. Identify which scenarios need process improvements and where additional training might help.
Attack Surface Analysis
Map incidents to specific systems, applications, and network segments to understand your actual attack surface. Identify which assets are targeted most frequently and require additional protection or monitoring.
False Positive Optimization
Analyze alert patterns to identify rules generating excessive false positives. Reduce alert fatigue by fine-tuning detection rules based on historical incident data and actual threat patterns.
Frequently Asked Questions
Can Sourcetable handle large volumes of security incident data?
Yes, Sourcetable processes millions of security events efficiently. Our AI algorithms are optimized for security data analysis, handling everything from daily alerts to massive breach forensics datasets without performance issues.
How does Sourcetable integrate with existing security tools?
Sourcetable connects with popular SIEM platforms, ticketing systems, and security tools through APIs and direct data imports. You can pull data from Splunk, QRadar, ServiceNow, and other common security platforms.
Is my sensitive security data secure in Sourcetable?
Absolutely. Sourcetable implements enterprise-grade security including end-to-end encryption, SOC 2 compliance, and granular access controls. Your incident data remains completely private and secure.
Can I create custom security metrics and KPIs?
Yes, you can define custom security metrics beyond standard MTTD and MTTR measurements. Create KPIs specific to your organization's security goals and automatically track them across all your incident data.
How long does it take to set up security incident analysis?
Most security teams are analyzing incidents within hours, not weeks. Import your data, and our AI immediately begins identifying patterns and generating insights. No complex setup or specialized training required.
Can I share security analysis results with non-technical stakeholders?
Definitely. Sourcetable creates executive-friendly reports with clear visualizations and plain-English explanations. Transform technical incident data into business-relevant insights that executives and board members can understand.
Frequently Asked Questions
If your question is not covered here, you can contact our team.
Contact Us