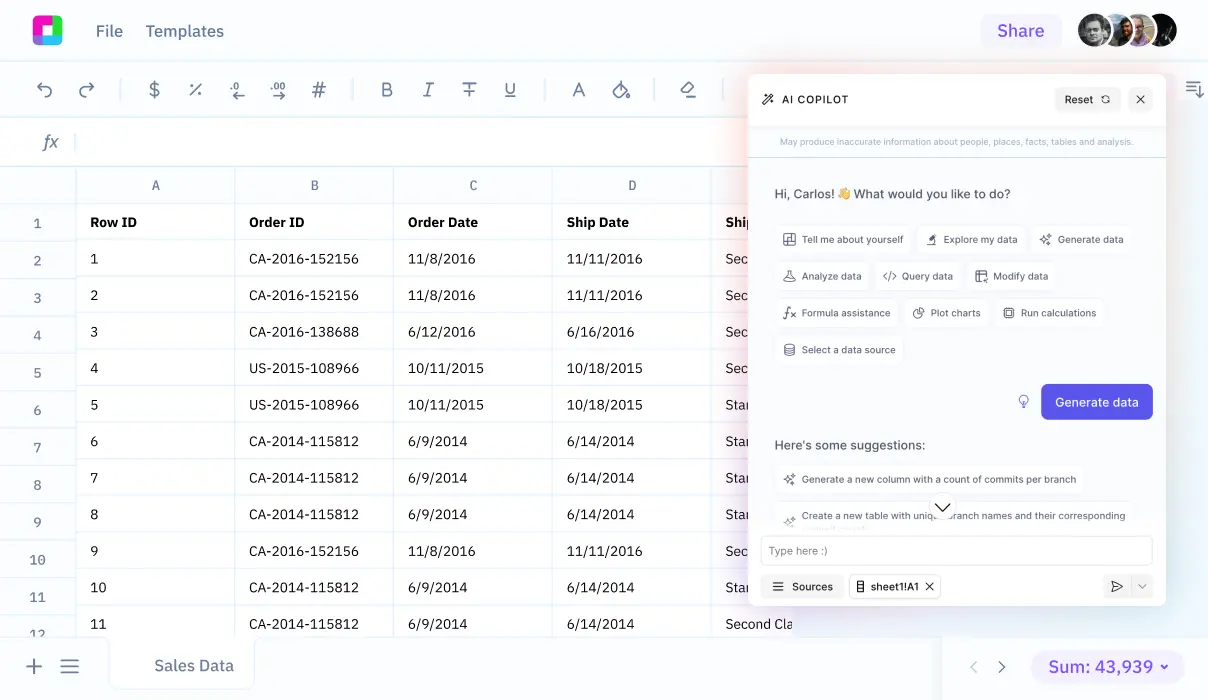
Picture this: You're drowning in security alerts, firewall logs, and vulnerability reports. Your SIEM is generating thousands of events daily, but which ones actually matter? You need to brief leadership on your security posture, but translating raw data into executive-friendly insights feels like speaking a foreign language.
Sound familiar? You're not alone. Security professionals everywhere are struggling with the same challenge: turning mountains of security data into actionable intelligence. That's where smart network security analysis comes in.
Why Security Teams Love Smart Analytics
Transform your security operations from reactive to proactive with data-driven insights
Spot Patterns in Chaos
Identify attack patterns, unusual traffic flows, and potential threats buried in thousands of log entries. Turn noise into signal.
Prioritize What Matters
Focus your limited time on real threats. Separate false positives from genuine security incidents with confidence.
Prove Your Impact
Generate clear reports that show executives exactly how your security investments are protecting the organization.
Predict Before Problems
Use historical data to anticipate security gaps and vulnerabilities before they become incidents.
Automate the Boring Stuff
Let AI handle routine analysis tasks so you can focus on strategic security improvements and threat hunting.
Collaborate Seamlessly
Share insights across teams without getting lost in translation. Everyone sees the same data, understands the same risks.
Security Analysis in Action
See how organizations use network security analysis to strengthen their defenses
Incident Response Timeline Analysis
A financial services company discovered their average incident response time was 4.2 hours. By analyzing response patterns, they identified bottlenecks and reduced it to 1.3 hours. The analysis revealed that 60% of delays occurred during the initial triage phase, leading to process improvements that saved millions in potential breach costs.
Vulnerability Assessment Prioritization
An e-commerce platform had 2,847 vulnerabilities flagged across their infrastructure. Using risk scoring analysis, they identified that just 23 critical vulnerabilities posed 78% of their actual risk. This focused approach allowed them to remediate the most dangerous issues first, optimizing their limited security resources.
Network Traffic Anomaly Detection
A manufacturing company's network showed unusual data transfers at 2 AM daily. Analysis revealed 15GB of data flowing to an external IP address - a clear indicator of data exfiltration. The pattern analysis helped them discover and stop an advanced persistent threat that had been active for months.
User Behavior Analytics
A healthcare organization analyzed login patterns and discovered that 12% of after-hours access attempts came from impossible geographic locations. This analysis led to the discovery of compromised credentials and implementation of stronger authentication controls.
Firewall Rule Optimization
A retail chain's firewall had 5,000+ rules accumulated over years. Analysis showed that 40% of rules were redundant or obsolete, and 200 rules were blocking legitimate business traffic. Cleaning up based on actual traffic patterns improved both security and performance.
Threat Intelligence Correlation
A technology startup correlated their security events with external threat intelligence feeds. They discovered that IP addresses from their logs matched known botnet command and control servers, revealing an ongoing attack campaign targeting their industry.
From Raw Data to Security Intelligence
Transform your security data analysis workflow in four simple steps
Import Your Security Data
Upload logs from firewalls, SIEM systems, vulnerability scanners, or any security tool. Support for CSV, JSON, XML, and direct database connections. Your data stays secure and private.
Ask Questions in Plain English
No need to learn complex query languages. Just ask: 'Which IP addresses have the most suspicious activity?' or 'Show me failed login attempts by country.' Our AI understands security terminology.
Get Instant Visual Insights
See attack patterns, threat distributions, and security metrics in clear charts and graphs. Identify trends, outliers, and correlations that would take hours to find manually.
Share and Act on Results
Generate professional reports for executives, create dashboards for SOC teams, or export findings to your security tools. Turn insights into action plans that strengthen your defenses.
Essential Security Analysis You Can Perform
Threat Detection & Pattern Analysis
Identify attack patterns, anomalous behavior, and potential threats in your network traffic. Analyze login attempts, data transfers, and access patterns to spot indicators of compromise before they become incidents.
Vulnerability Assessment Analytics
Transform vulnerability scan results into actionable remediation plans. Prioritize patches based on actual risk, track remediation progress, and demonstrate security improvements over time.
Incident Response Metrics
Measure and improve your incident response capabilities. Track response times, identify process bottlenecks, and optimize your security operations based on real performance data.
Compliance Reporting
Generate automated compliance reports for frameworks like SOX, HIPAA, PCI DSS, and ISO 27001. Demonstrate security controls effectiveness with clear metrics and documentation.
Security Tool ROI Analysis
Prove the value of your security investments. Analyze tool effectiveness, calculate cost savings from prevented incidents, and optimize your security budget allocation.
Common Questions About Security Analysis
How secure is my security data in Sourcetable?
Your security data is protected with enterprise-grade encryption both in transit and at rest. We use SOC 2 Type II certified infrastructure, support SSO integration, and offer on-premises deployment options for highly sensitive environments. Your data never leaves your control without explicit permission.
Can I analyze data from multiple security tools at once?
Absolutely. Import logs from firewalls, SIEM systems, vulnerability scanners, endpoint protection tools, and any other security solution. Correlate events across different data sources to get a complete picture of your security posture.
Do I need to be a data analyst to use this effectively?
Not at all. Our AI assistant understands security terminology and can help you analyze data using plain English questions. While advanced users can leverage powerful analytical features, the tool is designed for security professionals, not data scientists.
How does this compare to traditional SIEM solutions?
While SIEM tools focus on real-time monitoring and alerting, Sourcetable excels at post-incident analysis, trend identification, and strategic security planning. Think of it as the analytical companion to your existing security tools, not a replacement.
Can I create automated security reports?
Yes. Set up automated reports for executive briefings, compliance audits, or operational metrics. Schedule weekly threat summaries, monthly vulnerability reports, or quarterly security posture assessments that generate and distribute automatically.
What types of security data formats are supported?
We support virtually any data format including CSV, JSON, XML, database exports, and direct API connections. Common formats from Splunk, Elastic Stack, QRadar, ArcSight, and other security platforms work seamlessly.
How quickly can I get insights from my security data?
Most analyses complete in minutes, not hours. Simple queries return results instantly, while complex correlations across large datasets typically complete within 5-10 minutes. Much faster than traditional security analytics tools.
Is there a limit to how much security data I can analyze?
Plans scale with your needs. Analyze everything from small network logs to enterprise-scale security datasets with millions of events. Processing power scales automatically based on your data volume and complexity.
Frequently Asked Questions
If your question is not covered here, you can contact our team.
Contact Us