When Security Data Becomes Your Superpower
Picture this: You're drowning in security logs, vulnerability scans, and incident reports. Every alert feels urgent, but which threats deserve your attention? Traditional tools leave you playing whack-a-mole with symptoms instead of addressing root causes.
That's where cybersecurity threat analysis transforms chaos into clarity. Instead of reactive firefighting, you get proactive intelligence that helps you stay three steps ahead of attackers.
Why Security Teams Choose Advanced Threat Analysis
Discover the key benefits
Pattern Recognition at Scale
Spot sophisticated attack campaigns across thousands of data points. Identify coordinated threats that traditional tools miss completely.
Risk Quantification
Transform vague threat levels into concrete business impact metrics. Show executives exactly what's at stake with dollar figures and probability scores.
Predictive Intelligence
Use historical attack data to forecast future threats. Allocate resources where they'll have maximum protective impact.
Automated Correlation
Connect seemingly unrelated security events into cohesive threat narratives. Reduce false positives by 80% with intelligent analysis.
Threat Analysis in Action: Examples That Matter
See how security professionals use advanced analytics to protect their organizations
Advanced Persistent Threat (APT) Detection
A financial services team discovered a months-long infiltration by analyzing subtle patterns in login times, file access, and network traffic. The analysis revealed coordinated activity across 47 user accounts that appeared normal individually but formed a clear attack pattern when viewed together.
Insider Threat Investigation
By correlating badge access logs, system usage patterns, and data transfer volumes, a healthcare organization identified an employee systematically exfiltrating patient records. The analysis showed abnormal after-hours access combined with unusual database queries spanning six months.
Supply Chain Attack Analysis
A manufacturing company used dependency mapping and vulnerability correlation to trace a compromise back through their entire software supply chain. The analysis identified the attack vector: a compromised third-party library that affected 23 internal applications.
Phishing Campaign Attribution
Security researchers analyzed email metadata, hosting infrastructure, and attack timing to link seemingly unrelated phishing attempts. The pattern analysis revealed a single threat actor running coordinated campaigns across multiple industries.
Common Cybersecurity Threats You Can Analyze
Modern threat analysis covers the full spectrum of cybersecurity challenges. Here are the most critical categories where data-driven analysis makes the difference:
Network-Based Threats
Endpoint Security Threats
Human-Centered Threats
How to Conduct Effective Threat Analysis
Discover the key benefits
Data Collection & Aggregation
Gather security logs, network traffic data, vulnerability scans, and threat intelligence feeds. Import from SIEM systems, firewalls, endpoint protection, and external threat databases into a unified analysis workspace.
Pattern Identification
Use statistical analysis and machine learning to identify anomalies, trends, and correlations. Look for indicators of compromise (IoCs), attack signatures, and behavioral patterns that suggest malicious activity.
Threat Attribution & Classification
Classify threats by type, severity, and likely origin. Map attacks to known threat actor profiles and tactics, techniques, and procedures (TTPs). Assign risk scores based on potential business impact.
Impact Assessment
Quantify the potential damage from identified threats. Calculate financial risk, operational disruption, and compliance implications. Prioritize threats based on likelihood and impact matrices.
Mitigation Strategy Development
Design targeted countermeasures for each threat category. Recommend specific security controls, policy changes, and resource allocations. Create incident response playbooks for high-priority scenarios.
Why Security Teams Choose Sourcetable for Threat Analysis
Traditional security tools lock you into rigid dashboards and limited analysis capabilities. Sourcetable gives you the flexibility of spreadsheets with the power of AI and advanced analytics.
Excel-Compatible Security Analysis
Import security data from any source - SIEM exports, vulnerability scans, log files, or threat intelligence feeds. Work with familiar spreadsheet functions while leveraging AI for pattern detection and risk assessment. Your existing security workflows integrate seamlessly.
AI-Powered Threat Detection
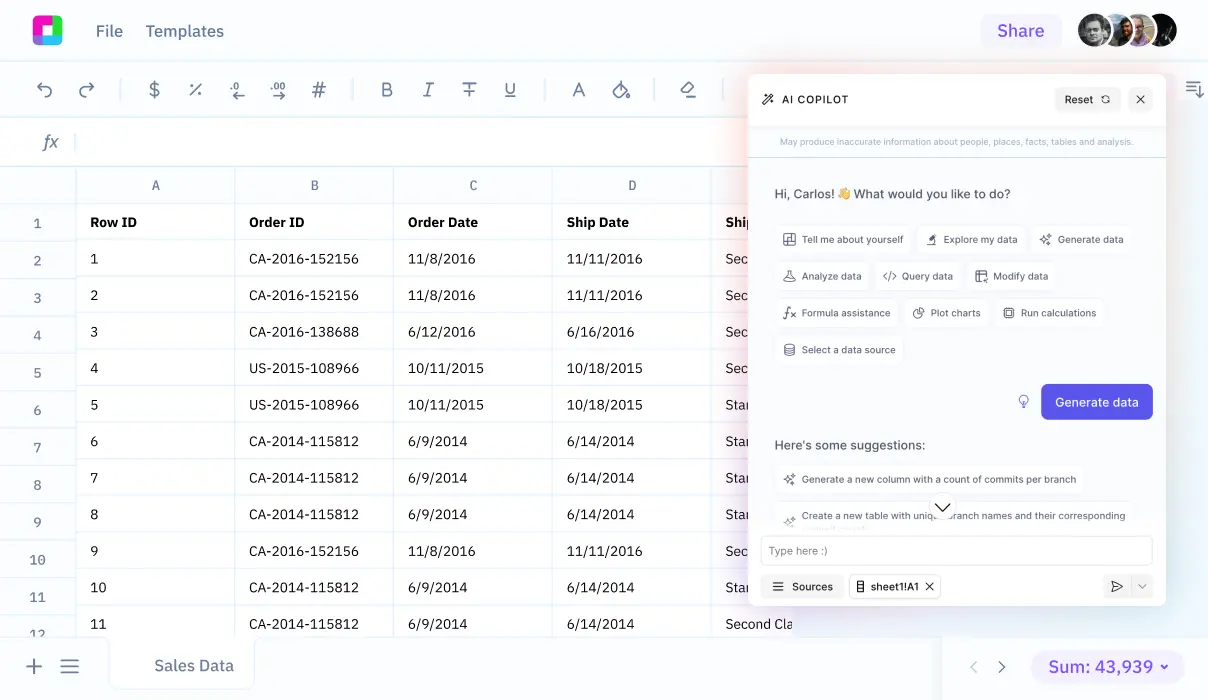
Ask natural language questions like "Show me unusual login patterns from the past 30 days" or "Which vulnerabilities pose the highest risk to our crown jewel systems?" Get instant analysis that would take hours to perform manually.
Real-Time Collaboration
Share threat analysis with stakeholders instantly. Security analysts, IT teams, and executives can all work from the same data with real-time updates. No more emailing static reports or fighting over file versions.
Start Your First Threat Analysis Today
You don't need specialized security analytics training to get started. If you can work with spreadsheets, you can perform advanced threat analysis with Sourcetable.
Step 1: Import Your Security Data
Upload CSV exports from your SIEM, firewall logs, vulnerability scanner results, or any other security data source. Sourcetable handles the heavy lifting of data normalization and preparation.
Step 2: Ask Questions in Plain English
Try queries like: "What are the most common attack vectors in our environment?" or "Show me failed login attempts grouped by source IP and time." The AI translates your questions into sophisticated analysis.
Step 3: Build Automated Monitoring
Set up recurring analysis to monitor key security metrics. Get alerts when threat patterns change or new risks emerge. Turn reactive security into proactive defense.
Frequently Asked Questions
How does AI-powered threat analysis compare to traditional SIEM tools?
While SIEM tools excel at log aggregation and basic alerting, AI-powered analysis in Sourcetable helps you understand the 'why' behind security events. You can ask natural language questions, identify complex patterns across multiple data sources, and get predictive insights that traditional tools miss. Plus, you're not locked into vendor-specific dashboards or query languages.
Can I analyze data from multiple security tools in one place?
Absolutely. Sourcetable ingests data from any source - firewall logs, endpoint protection, vulnerability scanners, threat intelligence feeds, and more. You can correlate events across your entire security stack without complex integrations or data transformation projects.
What types of threat patterns can the AI detect automatically?
The AI excels at detecting anomalies in user behavior, network traffic patterns, login attempts, file access, and system resource usage. It can identify coordinated attacks, privilege escalation attempts, data exfiltration patterns, and other sophisticated threats that might appear normal when viewed individually.
How quickly can I get actionable insights from my security data?
Most users see meaningful results within minutes of uploading their data. Simple pattern analysis happens instantly, while more complex correlation analysis typically completes in under an hour. The AI learns your environment over time, making subsequent analysis even faster and more accurate.
Is my sensitive security data safe in Sourcetable?
Security is our top priority. All data is encrypted in transit and at rest, with enterprise-grade access controls and audit logging. You can also run analysis on anonymized or aggregated data to maintain privacy while still gaining valuable insights. Many security teams use Sourcetable specifically because they can maintain full control over their sensitive data.
Do I need to be a data scientist to perform advanced threat analysis?
Not at all. If you can work with spreadsheets, you can perform sophisticated threat analysis. The AI handles complex statistical analysis, machine learning, and pattern recognition behind the scenes. You ask questions in plain English and get results in familiar spreadsheet format.
Frequently Asked Questions
If your question is not covered here, you can contact our team.
Contact Us