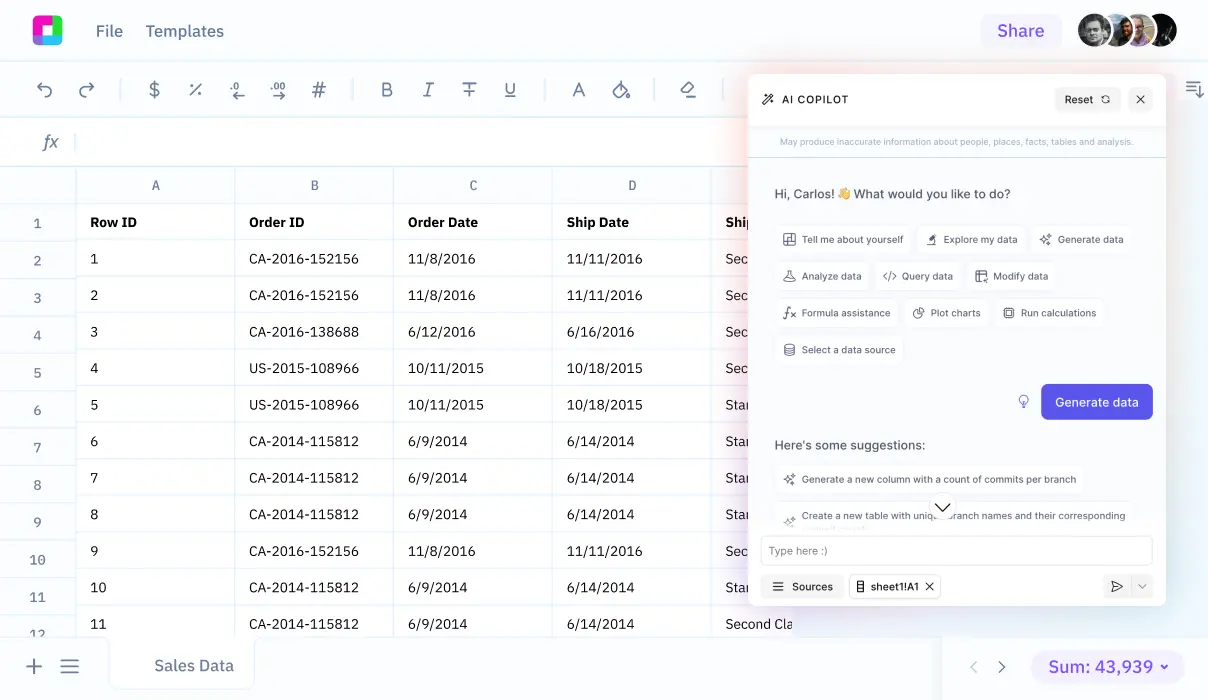
Every security professional knows the feeling: another incident report lands on your desk, and you're faced with the challenge of extracting meaningful patterns from what looks like chaos. Whether it's a data breach, malware outbreak, or insider threat, the ability to quickly analyze and understand incident data can mean the difference between containing a threat and watching it spread.
Traditional cybersecurity incident analysis often involves juggling multiple tools, copying data between systems, and spending hours creating reports that should take minutes. Sourcetable changes this by bringing AI-powered analysis directly to your familiar spreadsheet environment.
Why Security Teams Choose Sourcetable
Transform incident data into actionable intelligence with tools designed for security professionals
Real-time Threat Pattern Recognition
Automatically identify emerging attack patterns and anomalies across your incident data using AI-powered analysis
Automated Incident Correlation
Connect related incidents across different time periods and attack vectors to reveal coordinated campaigns
Response Time Analytics
Track and optimize your incident response performance with detailed timeline analysis and benchmarking
Risk Assessment Integration
Combine incident data with asset criticality and vulnerability information for comprehensive risk analysis
Cybersecurity Analysis in Action
See how security professionals use Sourcetable to transform incident data into strategic insights
Advanced Persistent Threat (APT) Campaign Analysis
A security team noticed unusual network activity across multiple endpoints. Using Sourcetable, they imported firewall logs, endpoint detection data, and user activity reports into a single analysis. The AI identified subtle patterns linking seemingly unrelated events over a six-month period, revealing a sophisticated APT campaign that traditional tools missed. The team mapped the attack timeline, identified compromised accounts, and developed targeted remediation strategies—all within hours instead of weeks.
Insider Threat Detection and Investigation
After suspicious data access patterns were flagged, investigators needed to correlate user behavior with access logs, email metadata, and file transfer records. Sourcetable's natural language queries allowed them to ask questions like 'Show me all users who accessed sensitive files outside normal hours in the past 90 days' and 'Which employees had unusual data download patterns before their departure date?' The analysis revealed concerning patterns that led to policy changes and enhanced monitoring protocols.
Phishing Campaign Impact Assessment
Following a company-wide phishing attack, the security team needed to assess the full impact quickly. They used Sourcetable to analyze email logs, user click-through rates, credential submission attempts, and subsequent system access patterns. The AI-powered analysis automatically categorized user responses, identified successful compromises, and generated risk scores for affected accounts. This comprehensive view enabled targeted remediation and informed security awareness training priorities.
Incident Response Performance Optimization
A security operations center wanted to improve their incident response times. They imported two years of incident data including detection time, escalation paths, resolution times, and severity classifications. Sourcetable's analysis revealed that certain incident types consistently exceeded SLA targets due to unclear escalation procedures. The team used these insights to redesign their playbooks and reduce average response time by 40%.
Your Security Analysis Workflow
From data import to actionable insights in minutes, not hours
Import Security Data
Connect your SIEM, EDR, firewall logs, and other security tools. Sourcetable handles CSV, JSON, XML, and API connections seamlessly.
Ask Natural Language Questions
Query your data using plain English: 'What are the most common attack vectors this quarter?' or 'Show me incidents with unusually long resolution times.'
AI-Powered Pattern Detection
Let AI identify correlations, anomalies, and trends that manual analysis might miss. Get instant insights into attack patterns and system vulnerabilities.
Generate Executive Reports
Create professional incident reports, risk assessments, and trend analyses with one click. Export to PDF or share directly with stakeholders.
Types of Cybersecurity Analysis
Sourcetable supports comprehensive cybersecurity analysis across multiple dimensions:
Threat Intelligence Analysis
Correlate internal incident data with external threat intelligence feeds. Identify indicators of compromise (IOCs), track threat actor techniques, and assess your organization's exposure to emerging threats. The platform automatically updates threat databases and highlights relevant matches in your incident data.
Vulnerability Impact Assessment
Combine vulnerability scan results with actual incident data to prioritize remediation efforts. Understand which vulnerabilities are being actively exploited and calculate business risk based on asset criticality and historical attack patterns.
Security Control Effectiveness
Measure the performance of your security controls by analyzing prevention, detection, and response metrics. Identify gaps in your security architecture and optimize control placement based on actual threat data.
Compliance and Audit Support
Generate compliance reports for frameworks like NIST, ISO 27001, or SOC 2. Track security metrics over time and demonstrate continuous improvement to auditors and stakeholders.
Frequently Asked Questions
How does Sourcetable handle sensitive security data?
Sourcetable employs enterprise-grade security including end-to-end encryption, SOC 2 compliance, and zero-trust architecture. Your security data remains encrypted at rest and in transit, with granular access controls and audit logging for all data operations.
Can I connect my existing SIEM or security tools?
Yes, Sourcetable integrates with major security platforms including Splunk, QRadar, Sentinel, and most tools that export CSV or JSON data. We also support API connections for real-time data feeds from your security infrastructure.
What types of incident analysis can I perform?
You can analyze any type of security incident including malware infections, data breaches, insider threats, phishing campaigns, network intrusions, and compliance violations. The platform supports both reactive incident analysis and proactive threat hunting.
How quickly can I get insights from my incident data?
Most analyses complete within minutes. Simple queries return results instantly, while complex correlations across large datasets typically complete in under 10 minutes. The AI-powered analysis runs continuously, providing real-time insights as new data arrives.
Do I need specialized security analysis skills?
No advanced technical skills required. Sourcetable's natural language interface allows you to ask questions in plain English. However, the platform is powerful enough for security analysts who want to perform sophisticated statistical analysis and custom queries.
Can I create automated security dashboards?
Yes, you can build dynamic dashboards that automatically update as new incident data arrives. Set up alerts for specific conditions, schedule regular reports, and share dashboards with your security team or executive leadership.
Frequently Asked Questions
If your question is not covered here, you can contact our team.
Contact Us